The Jigme Dorji Wangchuck National Referral Hospital is one of the top most renowned institutions in Bhutan delivering healthcare services. The hospital caters to the population of Thimphu and neighbouring districts.
The hospital not only functions as the National Referral Hospital for the entire country but also functions as a Regional Referral Hospital for the Western District, a District Hospital for Thimphu District, a Human resources pool and technical backup for District Hospitals, a Clinical training centre for the Royal Institute of Health Sciences (RIHS) and Technical support to the Public Health Programmes.
JDWNRH's challenges
As the hospital works round the clock, one of the major concerns was to manage complex shifts of employees. Elevator control, where only users with access rights can call the elevator, was another challenge the hospital wanted to meet.
Furthermore, the customer also wanted a solution, with the help of which the admin could assign entry and exit points for patients, visitors, and employees. Lastly, the management wanted to restrict visitor entry to a pre-defined time and rooms of the hospital for better visitor management.
Matrix's solution offered
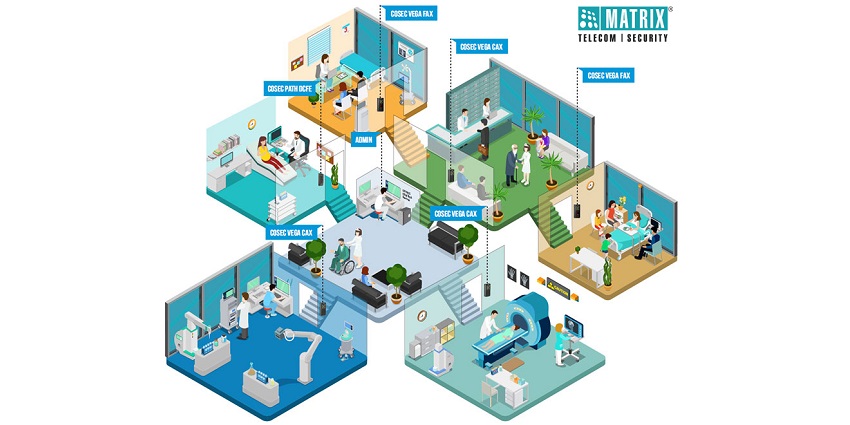
Around 206 devices were installed in the hospital that are used in controlling access to rooms and elevators
Matrix pitched its Access Control, Time-Attendance, and Visitor Management Solution along with the different variants of biometric devices, which fulfills every requirement of this renowned Hospital.
Around 206 devices were installed in the hospital that are used in controlling access to rooms and elevators. Devices were installed at the Main Entrance, Ward Rooms, Server Rooms, Outside Elevators, and at Ramps on every floor to restrict access. So, no individual in the building is not enrolled in the system.
Multiple shift management
As the Hospital works 24 hours, there are multiple shifts in which the employees work. Through this, the Hospital could manage multiple shifts of employees.
Approximately, 700 visitor profiles were created with constrained time to visit, limited rooms to enter, and a pre-defined route of access. Also, the crowd at the elevator was controlled by restricting the use to only users with elevator access rights.
Results
JDWNRH fulfilled its requirement with Matrix People Mobility Solution and achieved the following results:
- Improved security by restricting unauthorised entry using an access control solution.
- Reduced complexity of shifts by time-attendance solution.
- Crowd control through elevator access control.
- Time-based and zone-based entry restrictions for visitors and patients.
Products with the quantity used
- COSEC VEGA FAX (47) - Fingerprint and Card-based Door Controller for Time-Attendance and Access Control Application.
- COSEC VEGA CAX (65) - Card-based Door Controller for Time-Attendance and Access Control Application.
- COSEC PATH DCFE (28) - Fingerprint and Card-based Door Controller with IP65.
- COSEC PATH RDCE (66) - Card-based Exit Reader with IP65.
- COSEC ENROLL CARD (1) - Card Enrolment Station.
- COSEC ENROLL FINGER (1) - Finger Enrolment Station.
- COSEC VEGA CPM EM PROX (112) - EM Proximity Card Personality Reader Module for VEGA Series Door Controller.
- COSEC CPM EM PROX (1) - EM Proximity Card Personality Reader Module.
- COSEC CENTRA LE (1) - Application Server Platform with 1,000 Users and Expandable up to One Million Users for Basic Access Control and Raw Event Data.
- COSEC LE TAM (1) - Time-Attendance Module for COSEC CENTRA LE Users.
- COSEC LE ACM (1) - Access Control Software Module for COSEC CENTRA LE Users.
- COSEC LE VMM (1) - Visitor Management Module for COSEC CENTRA LE Users.
- COSEC USER100 (5) - User licence for 100 users.
Learn why leading casinos are upgrading to smarter, faster, and more compliant systems












