Access control systems are plagued by problems, such as false alarms and tailgating. Hakimo is a new company that applies concepts of deep learning to reduce false alarms and tailgating, and to make access control more accurate.
False or nuisance alarms from access control systems take a lot of time and attention for operators in global security operations centres (GSOCs). It’s wasted time they could use to perform more high-level duties. Hiring enough GSOC operators to monitor and resolve hundreds of nuisance alarms is prohibitively expensive. Fortunately, technology can perform the job.
Eliminating nuisance alarms
Eliminating nuisance alarms also makes operators more attentive to legitimate alarms
Eliminating nuisance alarms also makes operators more attentive to legitimate alarms, rather than disregarding them as background noise. There is much less chance that an actual alarm would get lost among the nuisance alarms.
“In many cases, users ignore alarms and become conditioned to think that every alarm is a false alarm,” said Samuel Joseph, the Co-Founder and Chief Executive Officer (CEO) of Hakimo, adding “It’s like the boy who cried wolf.”
Video and data analysis using deep learning
To address the problem, Hakimo analyses video and other data using deep learning, a form of artificial intelligence (AI) that employs a deep neural network, in order to emulate the operation of the human brain. Data passes through multiple non-linear layers for faster processing.
In the case of Hakimo, video of a door entrance or exit provides the data, and the system analyses quickly to verify an alarm and/or to ensure that only one person passes through a door, after a card swipe or other form of authorisation.
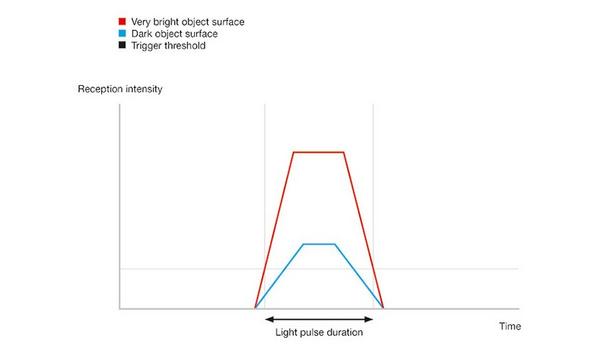
 |
| In an access control system with 300 doors, a GSOC might receive 100 nuisance alarms per day |
Multiple ways to generate nuisance alarms
There are many ways that an access control system can generate a nuisance alarm. For example, when a door closes, it sometimes ‘bounces’ on impact, because the magnetic lock has not yet engaged.
That bounce is mistakenly interpreted as a ‘door forced open’ alarm, by the access control system. Another example is if a faulty motion sensor on the inside of a door fails to detect a person exiting the building. Again, the result is a false ‘door forced open’ alarm. In an access control system with 300 doors, a GSOC might receive 100 nuisance alarms per day. The problem is multiplied even more, in the case of enterprise users with larger systems.
Hakimo’s approach fits well in vertical markets
Hakimo’s approach fits well in vertical markets, such as critical infrastructure (airports, utilities, etc.)
Hakimo’s approach fits well in vertical markets, such as critical infrastructure (airports, utilities, etc.), and technology and manufacturing firms. A typical user would likely have 200 or more doors, and 5,000 or so employees.
To address tailgating, Hakimo leverages deep learning to determine if a second person has followed closely behind someone, who has been correctly authorised to enter a facility.
Previously, many users ignored this possibly serious security flaw. In other cases, laser beam hardware was installed on the door frame to detect tailgating, integrated with the backend system. These systems are also prone to false alarms.
Deep learning algorithms detect tailgating
Hakimo’s deep learning algorithms detect tailgating and alert GSOC operators, when it occurs. In effect, it allows the access control system to keep the right people in and the wrong people out. Recent advances in artificial intelligence (AI) and deep learning enable the system, which performs tasks that were impossible just a few years ago.
Avoiding nuisance alarms has a straightforward return on investment (ROI). GSOC operators can be more efficient and have more available time to perform other important duties to secure an enterprise.
Minimising nuisance alarms and preventing tailgating
The deep learning system can also be applied to analyse stored access control data
Although more difficult to quantify, the possible costs and serious consequences of a security breach (tailgating) also make a strong case for embracing the technology. Most purchasers buy the system because of the combination of its benefits, both to minimise nuisance alarms and to prevent tailgating.
The deep learning system can also be applied to analyse stored access control data and to recognise anomalies that might suggest a security breach. For example, if a badge holder comes to work at an unusual time, the system can recognise the anomaly and call it to an operator’s attention. Although not a core feature of the system, it is one that some users leverage.
Bi-directional integrations with security systems
Hakimo, which was founded in 2020, has initially sold its system directly to end users, but is in the process of developing an integrator channel. They have on-boarded many integrators and continue to do so. They have also developed partnerships with major manufacturers for bi-directional integrations with access control and video systems. The list is growing.
Samuel Joseph adds, “A common misconception among users is that AI system algorithms take time to ‘learn’ how to function optimally in an application. However, in the case of Hakimo, the system works right out of the box.”
From facial recognition to LiDAR, explore the innovations redefining gaming surveillance