Technology & Trends - CCTV
Today, a number of school districts are saying no to these kinds of realistic active shooter drills In the wake of the shootings at Columbine High School in 1999 — 16 years ago — and the school shootings that have followed, we have struggled to figure out how to keep students and teachers safe during such an attack. Protective measures An approach to the problem that has grown controversial is armed assailant or active shooter drills. Six states including Arkansa...
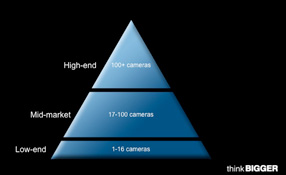
See bigger image Old pyramid w # of cams It’s clear that the network-based physical security industry has matured rapidly over the past few years. As the technology and other components of security solutions have advanced, so too have the customer’s expectations. Security solution companies must evolve in order to meet these new expectations. This requires an understanding of both the technology and the customers’ motivators, issues and hot buttons. Arr...
Stowaway incidents in the last two months in the United Kingdom have dramatised the desperate nature of individual attempts to cross borders. They have also exposed the callous methods of human traffickers. Sixty-eight foreign nationals were discovered in four lorries at the port of Harwich on the south coast of England in June after the vehicles had disembarked from a Stena Line ferry entering English waters from Holland. None of the group, which included 15 children and tw...
The great increase in the amount of data is driving physical security to the cloud Physical security is migrating to the cloud — because it improves the performance of physical security technology while holding down costs. “Essentially what is happening is that physical security technologies are growing more powerful and generating more and more data,” says Steve Surfaro, business development manager and security industry liaison with Axis Communications, wh...
The nature of crime in general – and particularly types of theft – are changing. Craig Mackey, Deputy Commissioner of London’s Metropolitan Police Service, says falling rates of conventional “property” crime are being of offset by an increase in computer-related crimes. Fall in “property” crime rate Mackey stressed that there has been no “magic bullet” responsible for the pronounced fall in burglaries and other prope...
In the vast centre of the hall almost none of the randomly shaped stands display their index number I enjoy IFSEC each year, spending three days walking the halls. I do feel frustrated by the acres of "me too" products prompting a "meh" response. So often I’m left feeling the "big news" is that hype and lies are growing and continue to drown out the truth. If companies' marketing budgets were simply given over to their product development departments, we would find thing...
When asking exhibitors at IFSEC International 2015 about what drives their markets, many cite system integration as a key factor. And they want more of it. Integration as business “driving force” For example, John Davies of TDSI says customers are now seeking out system integration. “They want a solution rather than components, such as linking access control with building management systems or with an organisation’s IT network to control access to its computers,”...
Security beyond its traditional boundaries is a big theme at IFSEC 2015 The security landscape is changing. Touring exhibitors on the first day of IFSEC International in London, it seems an increasing number of vendors are offering products that go beyond what may be termed "security," offering solutions for applications such as health and safety and data collection. They are also offering more smart technology with mobile phones and tablets, and are selling smarter by tailori...
Although in many cases CCTV has been an effective investigation tool, its full potential is not being realised It’s all very well installing CCTV cameras, but to be effective users have to know what to do to make images available to the police and courts, according to detective chief inspector Mick Neville of the Metropolitan Police. Although in many cases CCTV has been an effective investigation tool, its full potential is not being realised, says Neville, who is due t...
A retail banking tipping point is fast approaching with the state-side adoption of EMV technology Banking faces a challenge: to reconcile major security concerns with improving technology in order to reflect modern, mobile technology and the self-service solutions that customers have come to expect from their non-banking retail experiences. This is probably the number one issue I discuss with my bank clients. Banks need to make the technology in their branches more automated,...
This year's IFSEC International show in London will provide a reflection of the physical security industry's rapid growth, especially in the video sector, says one industry observer who is also a speaker at the show, coming up 16-18 June. “If we look at the overall trend, it is no surprise to anyone that IP is driving the growth and the future of the security business,” says Jim McHale, managing director of research company Memoori, and a speaker at IFSEC. Secur...
Security is a big concern for local government buildings, but there are measures that can make a difference Back in August of 2013, Rockne Warren Newell, armed with a rifle and a handgun, stormed a township meeting in the Ross Township Municipal Building in Saylorsburg, Pa. Witnesses say he fired through a wall into the meeting room and then burst into the room itself, guns blazing. Three people died, and two sustained wounds before citizens attending the meeting restrained hi...
Organisations are looking for ways to maximise resources and extract value from video security investment "There’s valuable information hiding within surveillance video. Extracting it can make a security department more efficient and provide a clear return on investment to their organisation." - Dror Irani, CEO and President, BriefCam - The Video Synopsis company. Challenges of video surveillance Video surveillance systems are a blessing to security. They are also a cu...
Managed and hosted services allow users access from a variety of connected devices It’s not about hardware anymore, although quality components are a must. Now, it’s about how technology performs. For the systems integrator, there’s also an opportunity to provide essential services to keep customers connected. As with many other businesses, the security industry is being “disrupted” and influenced by the cloud. Delivering outsourced security and...
Unrealistic promises by over-enthused marketers and under-delivery by R&D departments have damaged the cause of video analytics almost since its inception. For me, the exaggeration reached its worst point when industry pundits suggested that we would soon be able to identify and alert on anomalous behaviour of the kind demonstrated by the Tsarnaev brothers in the moments before the 2013 Boston Marathon Bombings. Mainstream journalists speculated that the two Chechen broth...
The future will produce cost-effective solutions that can provide meaningful coverage of wide expansive areas The greatest trend in history will continue to change the world, and the physical security market. It’s called Moore’s Law. In accordance with Moore’s Law, our electronics have consistently doubled in speed, halved in size, or halved in price every two years for decades already. This trend means that our electronics, communications networks, data ne...
Strategic management of costs is important when considering video storage systems Costs are at issue when considering any component of a video system. Strategic management of costs is especially important when considering video storage systems because storage accounts for such a large cost component of networked systems. Gartner’s Total Cost of Ownership (TCO) As enterprise products begin to dominate the video storage market, more attention needs to be addressed to Gar...
Integrators and end users should be aware that their definition of open might differ from those of security manufacturers Much of the buzz in the industry today about open architecture is driven by the IT world, with many security-related decisions now falling on an organisation’s IT department, where true open architecture has been around for a long time. Closed systems like we’ve experienced in the security world are not just viewed as foreign to the IT world; th...
Not too long ago the idea of home automation was strictly the province of the rich and famous. With costs that soared as high as $100,000 or more, controlling HVAC, lighting, doors and security from a single source just wasn’t in the budget for Main Street America. That was then, but now is an entirely different story. The “connected home” in which smart phones and tablets serve as controllers for Internet-enabled devices has gone mainstream. Installers are still fashioning hi...
The fundamental value of data is widely apparent in modern society, and its loss may have significant consequences Video data is critical to today’s enterprise. The latest video storage systems must offer dependable operation that doesn’t risk loss of that critical data. DDN - When performance matters “Not only is bandwidth very important, but functionality cannot be lost when a storage system is having a bad day,” says Jeff Adams, director of sales,...
According IHS Technology, more than 11 million consumer and DIY network cameras will be shipped worldwide this year Perhaps we should start looking at do-it-yourself (DIY) systems such Google’s Nest and other devices as an opportunity for existing security contractors – those that are open-minded anyway – to bring in additional customers and new streams of recurring monthly revenue (RMR). DIY systems continue to proliferate in the marketplace and are availab...
“Better, Faster, Cheaper – choose any two” is the old adage for computerised systems. When it comes to businesses subjected to federal or industry security regulations, the equivalent saying might be, “mitigate risk, achieve compliance, or reduce cost – choose any two.” So if there were a way to have all three that would get your attention. Complying with regulations More and more industries are subjected to some form of regulation....
Most of us have a basic instinct as to what is and is not ethical behaviour. But is instinct enough? “Ethics and the security industry is a balancing act,” says Mike Hurst, vice chairman of the UK Chapter of ASIS International. “Most people will have an instinct as to what ethical behaviour is, but there’s an absence of hard and fast rules.” Examples often crop up in video surveillance situations, Hurst says. For instance, when and where i...
SWOT evaluates a company’s Strengths, Weaknesses, Opportunities and Threats (SWOT) in connection with a project Expanding into other countries with sales offices, manufacturing facilities and distribution centres can present a number of security risks. SWOT analysis for security strategy Physical security technology can help to mitigate some of these risks. “The physical security technology used in international locations is similar to what we use here, but t...
The trend towards greater unification is facilitated by an all-encompassing shift to IP technologies As more organisations are looking for ways to maximise resources and increase operational efficiencies, unification of multiple security and business systems is gaining popularity. From the central command center, there is significant time lost when operators have to jump from video surveillance to access control systems to analyse an incident and take appropriate measures. Eve...
Maricopa County installed a fully integrated security controls system, featuring a VMS Larger IP video systems require plenty of storage, and several high-profile applications help to demonstrate the value of storage in today’s networked video environment. Maricopa county security project One example is the Maricopa County (Ariz.) Sheriff’s Office, which is nationally recognised for its zero tolerance toward crime and unwavering focus on innovation in law enforce...
Michael Byrden, Sales Director of ACT, considers the convergence of facility management. He describes how ACT, the access control manufacturer, has acquired a VMS and analytics development house in order to unify security solutions and bring customers nearer to the goal of a truly intelligent building. Desire for open systems Major acquisitions have been dominating the news recently and, even if this lays me open to a charge of naivety, I genuinely believe that they aren’t predatory. As...
Timm typically walks through school buildings to assess vulnerabilities, and recommends systems and products As an independent school security consultant, Paul Timm of RETA Security conducts security assessments and provides technical assistance for numerous school districts throughout the United States and Canada. Timm typically walks through school buildings to assess vulnerabilities, and recommends systems and products, practices and policies, and other strategies to optimi...
Since 2006, the LUSAX research program at Lund University in Sweden has investigated the effects of digitisation on the physical security industry. This article will look into the forces driving digitisation, and how those forces broadly translate and impacts the physical security industry. Historically, physical security systems have moved from purely mechanical systems into systems holding both mechanical and electronic low-voltage circuit-based components. Development was...
Just as with network switches, there are no real standards for midspans In general terms, a midspan is a power over Ethernet (PoE) power source that is placed between a network switch and the device being powered, hence the term midspan. The real question is, with almost all network switches providing PoE power, why do we need a midspan? The answer is, in some cases we don’t, but in others we do. As with any other product we have discussed, we need to first consider that...
Browse expert commentaries
Related videos
CLIQ Connect
DNAKE Access Control Terminals: Minimalist Design, Maximum Security!
Unlock the Future with Abloy Pulse: Keyless, Energy-Efficient Security Systems
Dahua Smart Dual Illumination Active Deterrence Network PTZ Camera
Hikvision DS-K6B630TX: Smart Pro Swing Barrier for Modern Access Control
Climax Mobile Lite: Advanced Personal Emergency Response System (PERS)
One system, one card
DownloadAligning physical and cyber defence for total protection
DownloadUnderstanding AI-powered video analytics
DownloadEnhancing physical access control using a self-service model
DownloadHow to implement a physical security strategy with privacy in mind
Download