The number of cyber attacks around the world has been steadily increasing year after year; for example, in 2022, the weekly rate of attacks on corporate networks was 38% higher than in 2021.
The potential financial losses of a data breach are substantial, with IBM's report putting the average cost at $4.35M. In order to reduce incidents quickly, organisations must take action and prevent them from happening in the first place. And using an interactive malware sandbox is a cost-effective and simple means of improving cybersecurity from the start. This article delves into the advantages this tool brings and how companies can benefit from it.
Potential financial losses
What is a malware sandbox? A malware sandbox is a virtual machine for malware analysis and dynamic testing. Security professionals use it to monitor malicious software and search for IOCs (Indicators of Compromise). These IOCs can inform endpoint detection systems and help protect future attacks. Here are five ways a sandbox can increase security for an organisation.
A malware sandbox is a virtual machine for malware analysis and dynamic testing
A malware sandbox increases email security - On average, one of every hundred emails that your organisation receives is a phishing attempt and one out of two hundred emails contains malicious software. Email is by far the most popular attack vector.
A single employee opening an infected document, likely sent in a way that the recipient is unaware of any danger, can cause the entire system to be breached. To reduce your risk of being infected, you should teach your staff about the potential harm of spear-phishing and phishing scams, as well as utilise a malware sandbox for scanning and verifying the threats.
- First and foremost, employees should be able to spot a suspicious email.
- Instead of immediately opening it, they should seek the help of an experienced defence professional.
- Cybersecurity experts can then analyse the suspect object in a sandbox environment.
- The analysis usually takes no longer than minutes and at the end, a report is generated.
- If it turns out to be a false alarm, then employees can carry on with the email with no harm done.
- But if it wasn't, you may have just saved yourself from potential disaster.
Safely detonating malware
A malware sandbox helps to analyse programs and links - Malicious emails are not the only form of payload delivery. Recently, criminals have begun to exploit Google Ads by creating replicas of open-source and commercial software to infect users.
Ads placed above organic search results often lead unsuspecting users to these infected versions
Ads placed above organic search results often lead unsuspecting users to these infected versions. The good news is that almost all malware requires some sort of user interaction to do damage, and sandboxes allow researchers to safely detonate malware in an isolated environment.
Suspicious network activity
A sandbox can help to respond to zero-day attacks quicker - Zero-day exploits have caused some of the most devastating attacks in history, like WannaCry ransomware and SolarWinds supply chain attack. While a sandbox won't prevent such incidents, it can help reduce their damage by allowing for quicker recovery. On average, companies can save $3M by reducing incident recovery time.
Let's say that a security professional notices suspicious network activity. They might immediately block the traffic stream with a firewall rule. But further investigation is still needed to determine how much of the system was compromised. Researchers can use a malware sandbox to execute the malicious file and collect the information about the processes, files, and network activity if created. Containment and eradication can then begin, such as developing a killswitch or restoring parts of the system from a backup.
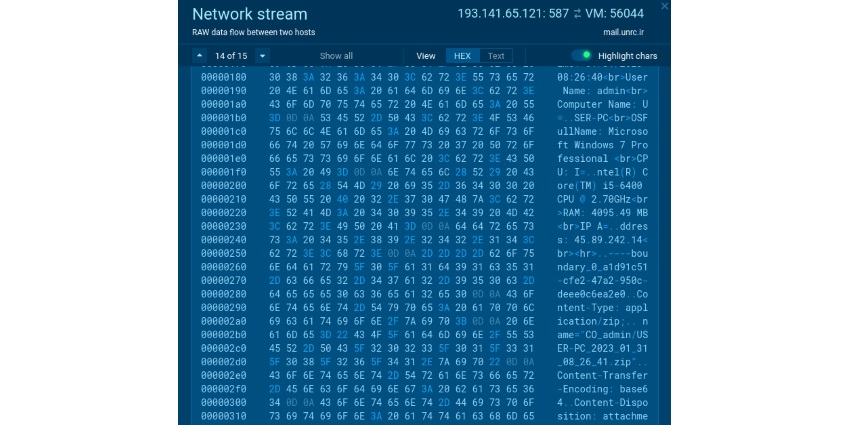 |
| Suspicious activity in the network traffic |
Anticipating future risks
A sandbox can strengthen your threat-based security - At this moment, there are more than a billion samples of malicious programs floating around the internet, and thousands of new variations being created every month. A major component of any organisation's security is being aware of the current threat environment and having the capability to quickly adjust tactics to anticipate future risks.
Cybersecurity experts use a variety of techniques to stay up-to-date on the latest threats
Cybersecurity experts use a variety of techniques to stay up-to-date on the latest threats facing their organisation and its users. These techniques can include reading reports written by other experts in the field, exploring underground malware marketplaces, and downloading new samples for analysis, and more. A malware sandbox can be a great tool for analysis, speeding up productivity for researchers by collecting IOCs in minutes and determining whether further investigation is needed.
Reverse engineering malicious code
A sandbox is a huge help when it comes to malware analysis - Analysing malware is tricky, time-consuming, and can put networks at risk if done incorrectly.
Because malware developers use code obfuscation and divide execution into stages to fool researchers, reverse engineering malicious code requires deobfuscating encoded strings, reconstructing functions that broken into parts are scattered across thousands of lines of code, and general head scratching.
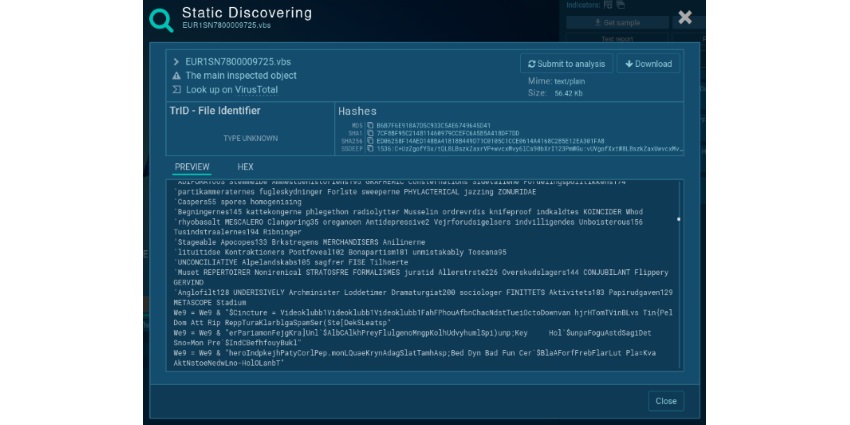 |
| It’s an analyst’s job to understand what this does |
Threat-based security
A malware sandbox, however, can do the same job in two minutes or less
Even with a familiar sample that may have some new obfuscation techniques, it can take an analyst at least 15-30 minutes to dig into the code and get to the key information. A malware sandbox, however, can do the same job in two minutes or less.
In summary, a malware sandbox can increase email security, help analyse programs, enable quick response to zero-day attacks, and strengthen threat-based security. Ultimately, it can help reduce the cost of potential data breaches, or prevent them entirely.
Stanislav Gaivoronskii is a malware analyst at ANY.RUN malware sandbox, the first interactive online malware analysis sandbox. He has more than 9 years of experience in the digital forensics field and 4 years in malware analysis.
Discover how AI, biometrics, and analytics are transforming casino security














