|
| In the last 10 years CCTV manufacturers have begun offering video search solutions aimed to reduce time and effort involved in searches |
Petabytes of security video recorded around the world every day. Obviously, we feel more secure knowing that we can “turn back time” and investigate the past – at least in situations for which video surveillance exists.
However, people who have experience requesting CCTV footage would say: “This takes way too much time.” So in many situations we aren’t able to take urgent action based on information that is already recorded and accessible!
Challenges in extracting and viewing CCTV video footage
“The hardest part of my job begins when my manager requests a video clip from the CCTV,” says Mike, a hotel security guard from San Francisco, California. “Normally they just describe the situation verbally, like ‘a guest has lost his bag in the lobby.’ So we don’t know when it happened, which doorman helped the guest with the bag, or where the bag was placed in the lobby. So it takes me hours (or even days!) to watch the footage. Don’t forget that I must be attentive to find the bag, so during this time I can’t do anything else.”
You hear similar complaints in other markets, too. “Every week we receive 10 to 20 requests mainly from ATM users and police,” says Peter, who works in the security department of a bank. “They all ask us to search in the footage. The descriptions they give are always indistinct, so we spend hours trying to export the clip. In some cases, due to low connection speed with the NVR, we have to travel to the location and sit there watching CCTV recordings for hours.”
It turns out that many CCTV users record video from their cameras and then can’t even use the video because of the manual work involved. Expenditures can be easily calculated if you total up guards’ salaries, idle time cost, penalties, etc.
Security video search solutions and types of searches
"The hardest part of my job |
However, in the last 10 years CCTV manufacturers have begun offering video search solutions aimed to reduce the time and effort involved in searches. Let’s look at five types of searches that can speed up the process and provide faster access to stored video footage. Also listed are the visual elements and the advantages and disadvantages of each type of search.
1. Time/date search
This is the classic search type. A user is supposed to know the time period during which the event has happened.
- Visual elements: Time/date input field, time/date selection, calendar.
- Advantages: The easiest and most popular search type.
- Disadvantages: The slowest approach. Requires specifying start and end time.
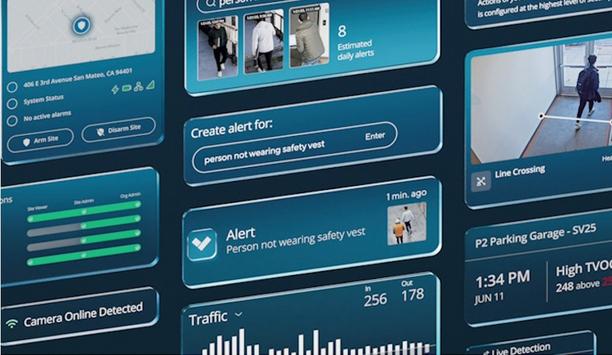
2. Event search
This search type is applicable if the video recorder can automatically identify events using video analytics or if it can receive and store events from an IP camera. The user can see the list of events, then filter and classify. Events may also come from external devices such as POS, ATM, etc.
- Visual elements: Event table, event filter.
- Advantages: Fast. Provides precise results.
- Disadvantages: Requires video analytics and event database. Sophisticated logic.
3. Thumbnail search
This search type can break down the footage to a number of screenshots/thumbnails that have significant scene differences. The user can visually identify a particular event among the screenshots.
- Visual elements: Thumbnail list
- Advantages: Fast, easy to use.
- Disadvantages: Works only with large objects; inefficient for search of more than two hours of footage.
4. Smart search
A user can select an area on the scene so the system will find changes in this area.
- Visual elements: Area selection with mouse.
- Advantages: Easy to use.
- Disadvantages: Slow; heavy CPU usage. In practice, it takes a lot of time to find an event. Low recognition level; inaccurate.
5. Forensic search (metadata search)
This search type allows users to search among massive footage. A user can specify object characteristics such as human/vehicle/pet, size of object, colour, speed, etc. Search results are provided immediately. This search type is based on metadata analysis.
- Visual elements: Object type, virtual line, area, size, colour, vector, speed selectors, text search fields.
- Advantages: Fast, precise, easy to use. Requires only a video stream.
- Disadvantages: Requires full-time storing of metadata.
Learn why leading casinos are upgrading to smarter, faster, and more compliant systems