 |
| Readily available security technology can help officials take control of their campuses |
Two top priorities for school security are the ability to communicate within a facility, and the ability to control access of who comes and goes. Paul Timm, president of RETA Security, an independent school security consulting firm, acknowledges the value (and popularity) of video cameras for school security, but that value is almost completely realised in terms of forensics – reacting after an incident rather than during or before. “Electronic access control and communication systems are more proactive and preventive,” he says.
Need for effective communication tools
Communications, specifically mass notification systems, are an important tool for school security, says Timm. “We have to make sure we have comprehensive coverage, meaning, can a staff member always have access to some kind of system that can get help, and provide information in an emergency?” Mass notification must be able to provide emergency information to people in the gymnasium, or on a field trip. “How do I get in touch with everyone in an emergency?” asks Timm. “Integrators are unveiling new things all the time.”
Timm cautions against depending on a common communication tool, especially among student populations – the cell phone. “Almost never will I allow a personal cellular phone as a primary means of communication. It may not be charged; they may not be getting a signal. They’re notoriously unreliable.” Providing emergency pendants to faculty is one option, Timm says.
Alerting via audio intercoms
 |
| See bigger image |
The use of audio intercoms provides immediate communications between campus administrators and classrooms, says John Mosebar, vice president, marketing, Aiphone Corp. The school office can simultaneously alert all teachers to provide specific commands such as lockdown or evacuate to a safer location. Teachers can also use the intercom system to contact the office for emergencies that originate in the classroom.
Role of visitor management systems
A second priority for school security is controlling access to the building. “How do we approve someone before they gain entrance into the entire building?” asks Timm. “What are the visitor management systems, and how do we make sure we are securing and restricting access to the building and also to the specific parts of the building?” In terms of “one button” lockdown systems, there are huge opportunities, he says: “The sky is the limit if you have funding.” However, a downside to one-button lockdown is the possibility that a teacher or group of students would be in the hallway at the time of the lockdown and unable to get safely back into the classroom.
Intercoms – video and audio – provide valuable layers of security for primary/secondary education campuses, says Mosebar. Think of video intercoms as a campus video doorbell. All visitors – parents, vendors, and even late-arriving students – have to request entry. School personnel then get to see and speak with the person before remotely unlocking the door. If there is any doubt, the door remains locked. By placing a video intercom at each campus entry – from the front door to the delivery dock – doors remain locked throughout the day, providing an effective barrier and greater security for students and staff.
Security begins at the entrance
Many school administrators now realise that campus security begins at the main entrance, says Mosebar. Without control of the entry, visitors may have unchecked access to classrooms and students. However, there is no one technology, product or service by itself that offers total entrance protection. A successful security plan makes use of layers of various technologies.
Layered security
Schools seem to be getting that message. When it comes to protecting the entry, a video intercom, mounted just outside the main door, is a key component allowing two-way voice-and-video identification with visitors. But a video intercom works best in conjunction with other complementary products including remote-controlled locks that allow staff to admit visitors while safely sitting behind locked doors. Security screens made of stainless steel mesh deter criminals willing to break door glass or adjacent windows to enter. Just inside the main door, an entry vestibule allows visitors immediate access only to the office and not classrooms. Also, a visitor management system helps keep track of visitors and identifies registered sex offenders and others with outstanding felony warrants.
Together, these components comprise an affordable solution that can be repeated easily across campuses of different age, design, size and use, says Mosebar.
By placing a video intercom at each campus entry – from the front door to the delivery dock – doors remain locked throughout the day, providing an effective barrier and greater security for students and staff. |
Readily available security technology can help officials take control of their campuses. The number of schools with open doors and without video intercoms or other surveillance cameras is becoming fewer in number. “It’s not as much a matter of security technology being underutilised, but rather if it is being used properly and cost-effectively,” Mosebar says.
Do more with less
The object of any solution is to eliminate or delay entry of an assailant long enough for police to respond and for school administrators to communicate with teachers and campus staff so they can lock down their classrooms or evacuate, depending on the situation. “Making sure the system is functioning and tested is the best practice to be prepare in case a situation arises,” says Mike Troiani, service manager for Idesco, a security integrator in the Tri-State area (New York, New Jersey and Connecticut). “Schools have lots of moving parts; they are always asked to do more with less.”
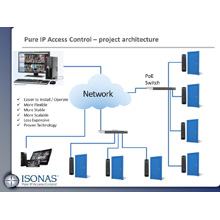
Isonas PowerNet reader/controller
IP access control systems are now finding their way into the education market, including the Isonas pure IP access control system. The Isonas solution eliminates all dedicated wiring and control panels by moving the technology into a single 1x6-inch reader/control at the door. Power is delivered to the reader/controller and to the electric strike or mag lock via power over Ethernet (PoE). Costs are dramatically reduced because no other electricity is needed at the door; the only wiring is Cat-5 Ethernet cable. The Isonas PowerNet reader/controller has the ability to hold 64,000 credentials, 5,000 events and 32 different time schedules. A school, or an entire district, can program permissions centrally and push the data to the reader/controllers at the edge. If the network goes down, the access control system does not fail because all decision-making can be made by the reader/controller. The result is an access control system that is 30 percent less expensive, deployed more quickly, with more flexibility than traditional panel systems.











