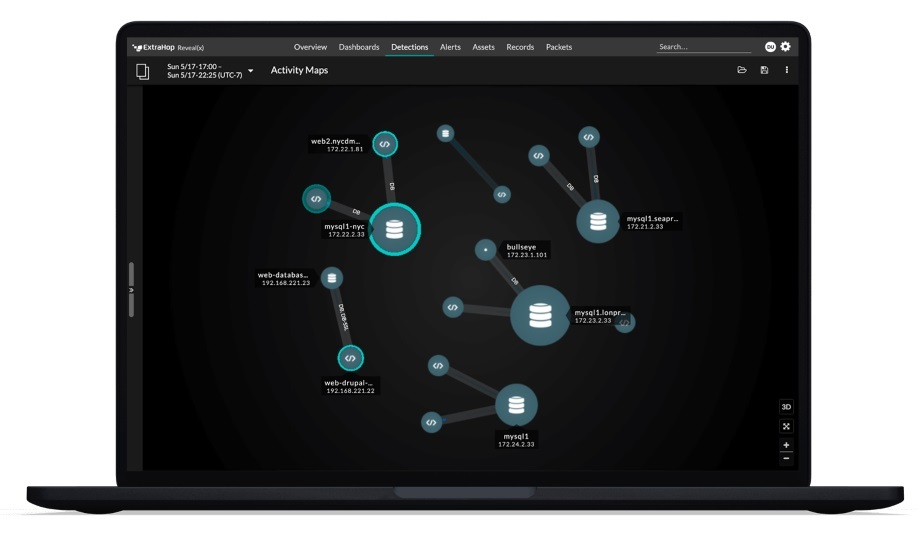
ExtraHop, the globally renowned provider of cloud-native network detection and response solutions, has announced the general availability of Reveal(x) 360, the first SaaS-based network detection and response (NDR) solution.
Reveal(x) 360 NDR solution provides on-demand, unified visibility across multi-cloud and hybrid workloads, as well as distributed workforces and operations.
Reveal(x) 360 SaaS-based NDR
With ExtraHop Reveal(x) 360, security operations teams can harness the power of the cloud to improve security posture without compromising availability or core business objectives.
Organisations around the world have experienced massive disruption as workforces rapidly transitioned to remote work and operations shifted off-premises. While the first phase of this shift focused primarily on making critical assets available to employees, the next phase will focus on how to enable that model long term and at scale.
Cloud and IoT digital transformation
Cloud, with its unlimited scale, OpEx pricing model, and global availability is suited for a distributed workforce
At the centre of that transformation are the Cloud and IoT. Cloud, with its unlimited scale, OpEx pricing model, and global availability zones, is ideally suited to enabling a distributed workforce.
At the same time, the need to support IoT has already increased exponentially as security and IT Ops teams contend with a plethora of employee devices accessing network resources.
Frictionless security
With Reveal(x) 360, ExtraHop combines the power of network data with the scale and speed of the Cloud to provide frictionless security from the data center to the Cloud to the user and device edge.
It is cloud-delivered, cloud-agnostic, and provides cloud intelligence for continuous protection across the entire attack surface.
Fully-integrated workflow
A fully-integrated workflow enables SecOps teams to manage detection, investigation, and response at scale and align to the demands of the business, even as IT and business realities continue to evolve.
- Cloud-Native Consumption Model - Reveal(x) 360 provides on-demand consumption, enabling customers to manage peak periods like Cyber Monday, fall course registration, and insurance enrollment periods without getting locked into annual contracts. On-demand consumption for index record search is available immediately, with additional on-demand purchasing options available in July.
- Centralised Management and Threat Visibility - A unified management pane provides complete visibility and control across multi-cloud workloads, data centers, remote sites, and users and devices all in one place. With centralised visibility, security teams can confidently detect, investigate, and respond to threats across the entire attack surface without switching between multiple point solutions trying to piece together the path of an attack.
- AI-Powered Threat Detection - Real-time intelligence and behavioral analysis derived from petabytes of anonymised threat telemetry collected daily makes Reveal(x) 360 cloud-based machine learning uniquely reliable, all without impacting sensor performance. Cloud-scale ML provides more than 1 million predictive models for a typical enterprise deployment to identify suspicious behaviors and potential threats.
- Real-Time Investigation - A cloud-based record store provides fully hosted and managed search capability for streamlined incident investigation with index record search and query of data from every segment of the hybrid environment.
- Continuous Intelligence - Reveal(x) 360 automatically updates detectors, threat intelligence feeds, and IoT profiles via the cloud, eliminating the need for manual intervention to ensure that policies or software on sensors are up to date.
Securing data centres, remote sites & cloud workloads
Over the past months, remote work, digital interactions, and online services have accelerated at an unprecedented rate"
“Over the past several months, remote work, digital interactions, and online services have accelerated at an unprecedented rate,” said Jesse Rothstein, ExtraHop Co-Founder and CTO.
Jesse adds, “And there is an increasing need to address significant gaps that have been exposed around both security and availability. Reveal(x) 360 is the culmination of a multi-year R&D investment to secure data centers, remote sites, and cloud workloads with frictionless deployment and actionable insights that can be securely accessed from anywhere.”
Reveal(x) 360 for multi-cloud and hybrid cloud environments is now available on AWS Marketplace. Flexible pricing plans include reserved instance and on-demand pricing options to align with individual customer budget requirements.
Customer reviews
“When you’re looking at investing in the rhythm of your business, there’s no other company that aligns to supporting the DevOps model—the speed, the lack of friction, than ExtraHop,” said Dan McDaniel, Chief Architect and Information Security Officer at Wizards of the Coast.
“Before ExtraHop, we had limited visibility into what was going on in the cloud, but with Reveal(x), we can quickly identify vulnerabilities and exploits and understand how our applications are performing in the cloud,” said John Kreis, Senior IT Engineer at Ulta Beauty.
Enhanced application, infrastructure security
ExtraHop makes it easy to monitor our environment and secure it, from remote desktops to cloud workloads"
“With ExtraHop, we’re able to monitor not only bandwidth and resources, but the security of our applications and infrastructure. With more and more of our workloads in the cloud, and now, with so many of our people working remotely, the level of visibility we get from ExtraHop in a single tool is just unmatched,” said a Senior Network Security Engineer for a large retail chain.
“ExtraHop makes it straightforward to monitor our environment and secure it, from remote desktops to cloud workloads,” said a Senior Manager for Security and Infrastructure at a West Coast healthcare provider firm.
Partner review
“Now that the dust has settled a bit since the initial transition to remote work, many of our customers are now looking to the future, thinking about how to support this forced transformation long term,” said Jonathan Wharton-Street, Head of Government and Education Sales, SBL.
He concludes, “Making sure you have a handle on every user and device accessing network resources is going to be critical to that. Reveal(x) 360 provides continuous visibility across every device and workload so that you never have to worry about what you don’t see.”
Learn why leading casinos are upgrading to smarter, faster, and more compliant systems