Technology & Trends - CCTV software
The potential costs and consequences of hackers getting through firewalls and onto the user’s computer networks can be devastating Theft of NATO data. Leakage of emails. Hackers setting up a live streaming website for over 100 New York City private webcams and even hacking the infrastructure servers of the U.S. government. As news of malicious takeover of private and corporate networks as well as incidents of malicious software programs, referred to as malware, conti...
NVR appliances ease analogue to IP transition by providing end users with a hybrid-ready product There should be a palatable migration path from a large installed base of analogue to the latest IP technology. The biggest missed opportunity related to network video recorder (NVR) NVR appliances in the video surveillance marketplace is effectively using existing analogue camera investments while transitioning to the network. For example, IP encoders can be utilised as a brid...
Aventura continues to expands expand its feature set of products beyond PSIM As the 61st annual ASIS 2015 kicked off in Anaheim, Calif., it became increasingly clear that physical security continues to move from the realm of traditional intrusion detection, video surveillance and alarms into value-added applications that extend into new markets, uses and purposes – many of them centred on business and operational processes. While video surveillance, intrusion detection,...
The potential is huge for vendors in the security and technology industries that have gun detection-related services & products Gunshot detection systems are a fast growing trend that helps police and security guards to protect the public, capture criminals and collect forensic evidence for investigations. Gunshot detectors use digital microphones installed on (or in) buildings or along streets that listen for evidence of gunshots, provide near instantaneous notification,...
NVRs of the past may have been expensive & complicated to use, but today NVRs have user-friendly functionality How much do you know – or think you know – about network video recorder (NVR) appliances? Manufacturers in the sector say there is a lot of misinformation in the market about these workhorse system components. We asked several manufacturers to help us set the record straight. A common misconception among end users is that NVRs lack features and reliab...
The pre-seminar will also offer educational sessions on cutting-edge subjects It is that time of the year again, when security industry stalwarts gather together at ASIS to showcase the latest in physical security systems and other technological innovations. The event will focus on domestic threats as well as intelligence gathering tools to protect organisations against social media threats. The organisers of the ASIS International 61st Annual Seminar and Exhibits — ASI...
Network video recorders (NVRs) are at the centre of today’s IP video systems. The video surveillance market includes a wide range of NVR choices for integrators and end users alike. NVR appliances include purpose-built machines that have embedded software systems as well as servers that are sold by video management system (VMS) software vendors and that have been pre-installed and preconfigured with their latest software capabilities. This article will take a look at s...
System integration is about adding value, and value-engineering is the solution to address the challenges facing the customer and their facility Leading systems integrators continue to embrace new technology and add a range of services focusing on IT, connectivity and integration. The trend will continue for forward-thinking companies seeking to differentiate themselves from the competition and gain a loyal following of end-user customers. Pref-Tech - History and backg...
Increases in the number of cameras and storage capacity have created an overabundance of video information that is difficult to manage Investment in video surveillance technology continues to increase as technology improves and security equipment becomes more affordable. Companies invest in video surveillance primarily to protect people and property, for both deterrence and more crucially for incident response. While there’s no doubt that the systems can provide a...
A 360-degree technology solution can be installed across the gaming floor, integrated right into the VMS and used for forensic purposes New 360-degree cameras are providing new video surveillance benefits to the casino market. MGM Resorts International has rolled out Oncam’s 360-degree technology solutions to the Aria, MGM Grand, Bellagio, Mirage and New York-New York properties along the Las Vegas strip. More specifically, the surveillance team at the Aria manages more...
9-11 caused a sharp refocus of attention on security assessment and risk management Fifteen to 20 years ago, security was a relatively sleepy, small-time business. Companies typically hired a guard or two to walk around the property, usually at night, sometimes during the day. If a guard spotted someone who wasn’t supposed to be there, he (it was usually a he) ran the person off. Larger companies had more sophisticated video and access control systems, but those system...
Successful video infrastructure management requires visibility into the network’s behaviour The importance of video in an organisation has been growing over the past several years, almost exponentially. In retail, video images can help detect or deter theft by employees and patrons. Casinos use video partly due to state regulations, to ensure gaming activity is free of deceit or fraud. Branch offices use video to communicate with the head office. Schools use video for di...
Any wireless device can be a soft target for hackers Security network hacking is one of the hottest topics today. The ability to access security systems or devices anywhere, leaves them vulnerable and prone to hacking. Any wireless device can be a soft target for hackers. Let’s start with the concept that nothing on a network is really secure. Let’s admit this to ourselves and take the next steps to make our security networks more secure. Internet of Things securi...
In casino surveillance, there must be an understanding of the behaviour of thieves and cheats. In particular, casinos must understand how the behaviour of a casino adversary differs from that of a legitimate guest. The end result of the understanding is that only threatening or fraudulent behaviour is challenged, leaving other guests free to simply enjoy their visits to the casino. Responding to behaviour anomalies requires understanding that comes from analytics capabilities...
Wavestore’s Better Together programme is designed to offer benefits to security installers and integrators An independent video management system (VMS) offers an open platform that can support the “best-in-breed” components of security systems, according to James Smith, director of marketing at Wavestore. “We offer a truly open platform and are truly independent – what we do really well is bring disparate technologies together,” says Smith....
The key driver to growth in the IP market is the effectiveness and efficiency of the technology Technological advances in video surveillance are allowing end users the flexibility to do more with their systems than previously imagined. 2014 saw several new technological trends that shaped the future of the security market, with 4K and cyber security being the main drivers. The drift continues this year too with end users demanding HD video surveillance and wide-spread...
Large busy casinos must maintain continuous surveillance of multiple tables and machines High-definition (HD) cameras are a perfect fit for the casino market. HD security cameras provide six times the resolution of analogue cameras, supplying images with sharper edges that easily identify faces, cards, dice, chips, currency, and fill slips. In addition, high-definition IP cameras can reduce camera count. A single, 1080p camera can effectively cover poker, roulette or craps tab...
This article by Keith Jernigan Sr., General Manager - MOBOTIX Corporation states the enormous impact of smart surveillance on various sectors. Highlighting the changing trends of video surveillance, Keith talks about the several benefits of IoT. He mentions that the new era will see video surveillance companies as more than just video security cameras sellers. To summarise, IoT is forecasted to conjure up businesses offerings, reduce costs and hazards, create jobs and opportunities, thus leading...
Security and technology are rushing to offer home automation solutions and build out the Smart Home of connected devices and applications. As cameras, alarms, as well as, thermostats and other appliances become controllable and programmable using Internet-enabled smart phones, they are becoming part of a vast web called the internet of things (IoT). Achieving greater value through smart data exchange This network of physical objects or "things" embedded with electronics, software, sensors and...
Affiliated Monitoring’s UL-Listed monitoring centre with a second floor dedicated to areas for security company meetings Central monitoring stations have innovative approaches to assist security installing companies in growing their account base, adding value and boosting recurring monthly revenue (RMR). These companies do much more than simply monitor accounts – today they provide a host of services to give security installing companies the added edge in an extrem...
For police, BWCs can significantly improve how evidence is collected by recording the visual and audio actions Body worn cameras (BWCs) are becoming common place in law enforcement. While the spotlight for body cameras is on police in the news, BWCs are also sought after in security-related contracts for airports, campuses, correctional facilities and for private security. It’s quite likely interactions with police or security guards will be recorded (people who re...
When video analytics first emerged in the security industry about a decade ago, there were high hopes it would instantly transform the landscape of video surveillance. Problem was, the technology was not mature and, in essence, was oversold as far as its capabilities. Analytics such as heat mapping, directional and license plate recognition technology have improved, lending themselves to applications beyond security and into the realm of actionable business intelligence Integra...
Potential deployments of video analytics, or my own preferred term “intelligent scene analysis,” are being worked on by some of the best minds at university campuses across the United Kingdom. Later this year I will visit Kingston University whose Digital Imaging Research Centre is one of the largest computer vision groups in Europe. Violence prevention through analytical intelligence Here, I talk to Prof David Marshall of Cardiff University, who describes work...
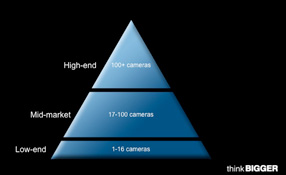
See bigger image Old pyramid w # of cams It’s clear that the network-based physical security industry has matured rapidly over the past few years. As the technology and other components of security solutions have advanced, so too have the customer’s expectations. Security solution companies must evolve in order to meet these new expectations. This requires an understanding of both the technology and the customers’ motivators, issues and hot buttons. Arr...
The great increase in the amount of data is driving physical security to the cloud Physical security is migrating to the cloud — because it improves the performance of physical security technology while holding down costs. “Essentially what is happening is that physical security technologies are growing more powerful and generating more and more data,” says Steve Surfaro, business development manager and security industry liaison with Axis Communications, wh...
When asking exhibitors at IFSEC International 2015 about what drives their markets, many cite system integration as a key factor. And they want more of it. Integration as business “driving force” For example, John Davies of TDSI says customers are now seeking out system integration. “They want a solution rather than components, such as linking access control with building management systems or with an organisation’s IT network to control access to its computers,”...
Unrealistic promises by over-enthused marketers and under-delivery by R&D departments have damaged the cause of video analytics almost since its inception. For me, the exaggeration reached its worst point when industry pundits suggested that we would soon be able to identify and alert on anomalous behaviour of the kind demonstrated by the Tsarnaev brothers in the moments before the 2013 Boston Marathon Bombings. Mainstream journalists speculated that the two Chechen broth...
Michael Byrden, Sales Director of ACT, considers the convergence of facility management. He describes how ACT, the access control manufacturer, has acquired a VMS and analytics development house in order to unify security solutions and bring customers nearer to the goal of a truly intelligent building. Desire for open systems Major acquisitions have been dominating the news recently and, even if this lays me open to a charge of naivety, I genuinely believe that they aren’t predatory. As...
Honeywell recently helped the Penns Valley Area School district in Pennsylvania design and implement a custom security system Security systems are just part of the solution to protecting primary/secondary schools. Technology can contribute to a broader, holistic approach to security that is customised to meet the needs of each educational institution. Honeywell has helped many schools customise security systems to meet each school’s unique needs, says Bruce Montgomery,...
see bigger image Figure 5: Providing correct and useful results requires intersection of user intentions, VCA interpretation, and results provided by VCA tool The term Video Content Analysis (VCA) is often used to describe sophisticated video analytics technologies designed to assist analysts in classifying or detecting events of interest in videos. These events may include the appearance of a particular object, class of objects, or action. VCA technology employs a comple...
Browse expert commentaries
Related videos
CLIQ Connect
DNAKE Access Control Terminals: Minimalist Design, Maximum Security!
Unlock the Future with Abloy Pulse: Keyless, Energy-Efficient Security Systems
Dahua Smart Dual Illumination Active Deterrence Network PTZ Camera
Hikvision DS-K6B630TX: Smart Pro Swing Barrier for Modern Access Control
Climax Mobile Lite: Advanced Personal Emergency Response System (PERS)
One system, one card
DownloadAligning physical and cyber defence for total protection
DownloadUnderstanding AI-powered video analytics
DownloadEnhancing physical access control using a self-service model
DownloadHow to implement a physical security strategy with privacy in mind
Download