The most terrifying thing about terrorism is its reliance on the element of surprise. Most people don’t see the attacks coming, or don’t recognise the indicators when they see them. When terrorists strike, law enforcement is disadvantaged, the victims shocked and by the time an effective response is mounted the perpetrators are often long gone.
Many security managers do not know that through careful antiterrorism planning they can increase their chances of effectively responding to a terrorist attack and in doing so, lessen the likelihood of an attack in the first place.
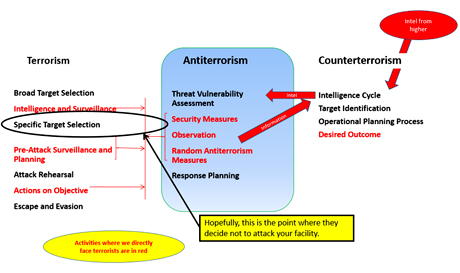
Antiterrorism and counterterrorism
Terrorism is an act of violence where the victim is not the intended target. When terrorists attacked the USS Cole in October of 2000, their victims were the crew of the warship, but the intended target was the US Government and its Middle East policies. It follows the same logic as a kidnap for ransom: the victim is the person stolen off the street and hidden away against their will, but the target is the relative or business with access to cash.
Antiterrorism serves the same end as counterterrorism, but they are different. Counterterrorism is the actions of the military, law enforcement and diplomats who work to apprehend or neutralise specific terrorist groups or individuals. Antiterrorism is the use of passive measures to harden targets and render them unattractive to terrorists. Antiterrorism and counterterrorism work together by providing each other with information: counterterrorism forces tell antiterrorism planners of general and specific threats and antiterrorism planners tell counterterrorism forces of unusual or suspicious activities in their areas that could indicate interest by a terrorist or terrorist group.
A TVA provides a realistic assessment |
Elements of an antiterrorism plan
There are five elements to an antiterrorism plan. It starts with a Threat Vulnerability Assessment (TVA), which provides a realistic assessment of who the terrorists are, what weapons, explosives, or tools that they use and what tactics and techniques they employ. We measure this information against the threat environment: do they exist? What are their capabilities? Do they have the capability and the intention to strike? Are they engaged in targeting right now? How competent are the counterterrorism forces at neutralising or defeating them? From this, we determine our threat level: Negligible, Low, Medium, High, or Critical. The next part of the TVA involves measuring vulnerability. We look in detail at the assets to be protected and we evaluate them against the range of threat types (potential attackers, weapons, tools, tactics and techniques) determined earlier. We then evaluate this information against the full range of threat levels. From this, we develop our Security Measures.
Effective security measures
The functions of effective security measures include access control, deterrence, intrusion detection, assessment, delay, response, or the collection and preservation of evidence. Planners must keep in mind that security measures cost time, money and convenience, so they should always seek to use the minimum appropriate to the threat and deploy or demobilise them as the threat of attack increases or decreases.
For example, the XYZ Processing Plant is designed to operate at a default threat level of Low. It is surrounded by a fence with CCTV cameras on the corners, perimeter lighting and a single guard at the gate. Plant security is told that the threat has been increased to Medium. They respond by positioning Jersey barriers beside the main approach to the plant, adding another guard, deploying a temporary and moveable CCTV camera and deploying a mobile patrol vehicle. If the threat level increased to High or Critical, then increasingly intrusive and expensive measures are applied. The measures are removed as the threat decreases back to Low.
 |
| Few successful terrorist attacks are ever launched without an extensive period of surveillance |
Observation plan
Few successful terrorist attacks are ever launched without an extensive period of surveillance. The attackers need to know a lot of information about the target before they can attack: how is it protected? What is its routine? When do the guard shifts change? When are the periods of maximum and minimum activity at the entrance or exit points? How do visitors, couriers and delivery trucks get in? This dependence on information creates an opportunity for antiterrorism planners and is addressed in the Observation plan. The part of the process that is the most active is Observation. Guards, security staff and employees are trained to watch for the following signs of terrorist activity:
- Surveillance of the facility, especially near entrances and exits
- Elicitation of information that may be useful to an attacker from guards or employees
- Testing the security at the facility (for example, a bogus 9-1-1 call placed near the facility to see how long it takes for law enforcement to respond)
- Unusual people around the facility that normally don’t belong, especially if they appear to be communicating with each other through looks, voice, or hand signals
- Deploying assets or getting into an attack position
The observation plan instructs |
Countersurveillance operation
The observation plan instructs people where to look, for what activity and to whom they should pass the information if something of interest is seen. Non-emergency information is passed back through security managers to counterterrorism forces. If, for example, there are indications that the facility is under surveillance, then counterterrorist forces will conduct a countersurveillance operation to determine the source of the surveillance and ultimately their intent. If a terrorist group is watching the facility, then a countersurveillance operation is the beginning of the end for them.
If it appears that an attack is imminent, then the observer would report straight to the local law enforcement emergency line, such as 9-1-1.
Random antiterrorism measures
How do we address a terrorist group that might be watching a facility without being detected? We randomly change the security measures used every day, complicating their attempts to figure out what the security plan is. These Random Antiterrorism Measures are particularly useful – they complicate terrorist attack planning and they sow doubt, as the terrorists may suspect that they’ve been discovered and that the changes are a response to it. For example, on Monday they might observe that there are two guards at the gate. On Tuesday, there are three. On Wednesday, they see two guards as the gate, but they are checking the identification of everyone who passes through. On Thursday the two guards have suspended ID checks, but instead are randomly checking the trunks and backseats of all vehicles going through the gate. On Friday there is a police cruiser parked near the gate for several hours. By then, the terrorists don’t know what to expect the next day and will likely determine that it is too hard a target and will move on.
 |
| Success in antiterrorism is not random at all, but is the result of careful analysis, planning, and execution [view larger image] |
Response planning
Response planning is something that most facilities do, but in addition to the usual fire and evacuation planning, they should include actions upon discovery of suspected or real surveillance and all the activities watched for in the Observation plan. Included in response planning should be all the potential scenarios identified in the TVA.
Preventing terrorist attacks is a process by which we convince the terrorists that they are unlikely to be successful and by doing so inducing them to move on. Success in antiterrorism is not random at all, but is the result of careful analysis, planning and execution.
Understand how converged physical and cybersecurity systems can scale protection.














