Visitor management systems - Security beat
Companies at GSX 2023 emphasised new ways that technologies such as artificial intelligence (AI) and the cloud can address long-standing issues in the security market. Among the exhibitors at the event in Dallas were companies seeking creative ways to apply technology, lower costs, and make the world a safer place. Reflecting on the exhibition, here are some additional takeaways. Expanding AI at the edge i-PRO is a company reflecting the continued expansion of edge AI capability in the...
Casinos offer several attractive applications for LiDAR, including security and business intelligence. Using laser sensors, the technology can replace the use of surveillance cameras. For casino security, LiDAR can track player movement and provides complete coverage and accuracy that have not been achievable by surveillance cameras. Massive coverage areas can save on costs of sensor deployment versus other technologies. LiDAR and its applications LiDAR is a method for determining ranges by t...
Newer facial recognition systems are scalable and provide more accurate results, and the end-user selects the parameters of system performance to suit their own application needs. “We have developed algorithms that can be optimised in various compute environments, whether in a small chip inside an edge device or on a large server device,” says Ido Amidi, Oosto’s Vice President of Products and Business Development. “It all depends on client needs. We can do it all withou...
It’s been almost exactly a decade since HID Global launched the world's first university pilot of smartphones carrying secure mobile IDs. A lot has changed in the following 10 years. Today’s technology has matured, advanced, and proliferated across a variety of high-value use cases. To catch up on the latest developments in mobile access, we contacted Luc Merredew, Product Marketing Director, Physical Access Control, at HID Global. Q: What has changed since the first pilo...
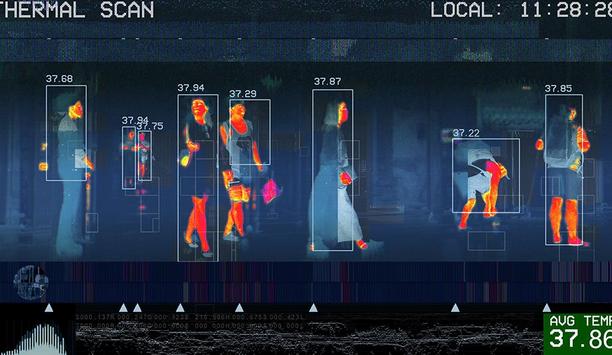
Thermal cameras can be used for rapid and safe initial temperature screening of staff, visitors and customers. Used the right way, the cameras can help prevent unnecessary spread of viruses like the novel coronavirus. During the global pandemic, use of thermal cameras has increased, but they have not always been used correctly, and therefore, not effectively. Hikvision’s temperature screening thermal products are currently assisting users in initial temperature screening across the global...
The coronavirus pandemic had a monumental impact on all aspects of the business world, including the security industry. However, amid the gloom and doom, many security professionals also saw opportunity: New ways the industry’s products could be applied to address the challenges of coping with the virus. This article will review some of those opportunities, based on our reporting throughout the year and including links back to the original articles. During and after the pandemic, security...
Video, access control and visitor management are among the technologies that are enabling greater safety and security at hospitals and other healthcare facilities. Video surveillance systems enable hospital management and security professionals to know what goes on in and around a medical facility. Recording images in high resolutions (megapixels and gigapixels) is becoming more and more important in healthcare, says Jason Ouellette, Product Line Director – Access Control, Tyco Security P...
When violence or a life-threatening incident occurs, hospitals and other healthcare institutions are often in the crosshairs. Hospitals increasingly face a reality of workplace violence, attacks on patients, and threats to doctors and other support staff. And even if violence happens outside a hospital – such as an active shooter at a public place – the local hospital must be prepared to respond to an influx of injured victims. When conflicts arise inside a hospital, there is an urg...
All schools and universities need to address three different levels of security when considering access control. The first level is the least vulnerable of the three and concerns the perimeter entry and exit points. Here, incorporating some level of electronic access control should be a consideration, whether that is a combination of electronic and mechanical door hardware, or a complete electronic solution. An electromechanical solution, such as electric strikes, can be beneficial in the effec...
Time for an indepth review of IFSEC 2019 in London. This show had fewer exhibitors than previous shows, and the ‘vibe’ was definitely more low-key. Fewer exhibitors meant larger aisles and plenty of room to breathe, and the slower pace provided time for exhibitors to reflect (often negatively) on the return on investment (ROI) of large trade shows. There was little buzz on the first day of the show, but spirits picked up on the second day (when, not coincidentally, some exhibitors...
Facial recognition has seen huge breakthroughs since the U.S. National Institute of Standards and Technology (NIST) first began testing in 2010. Accuracy has seen massive gains, especially from 2013-2018. In the 2018 test, the most accurate algorithm was 20 times more accurate than the 2013 equivalent. Essentially, 95 percent of the matches that failed in 2013 now yield correct results. Compare that to 2010-2013, when the most accurate algorithm reduced its error rate by 30 percent. This reduc...
Attendance has been growing steadily year-over-year for ISC West, and the 2018 show exceeded 30,000 total industry visitors for the first time. So it’s safe to expect ISC West 2019, April 10-12 at the Sands Expo in Las Vegas, will be bigger than ever. Preregistration for the 2019 show is on track to bring even more visitors than last year. “This is a show for everyone, for converged security,” says Mary Beth Shaughnessy, Event Director for Reed Exhibitions. “We bring a l...
How’s this for a simple access control scenario? You walk up to a door, wave your hand in front of a button, the button lights up, and the door opens. That’s the simplified user experience that startup Openpath is promoting as it enters the crowded and mature market for physical access control. Openpath says a simple user experience provides the extra boost needed for mobile credentialing to gain momentum. In this case, it’s even simpler than using a card credential (no s...
ADT Inc.’s acquisition of Red Hawk Fire & Security, Boca Raton, Fla., is the latest move in ADT Commercial’s strategy to buy up security integrator firms around the country and grow their footprint. In addition to the Red Hawk acquisition, announced in mid-October, ADT has acquired more than a half-dozen security system integration firms in the last year or so. Here’s a quick rundown of integrator companies acquired by ADT: Protec, a Pacific Northwest commerc...
The Global Security Exchange (GSX) seems smaller this year, which is not surprising given the absence on the show floor of several big companies such as Hikvision and ASSA ABLOY (although their subsidiary HID Global has a big booth). A trend affecting the number of companies exhibiting at GSX 2018, and other trade shows, is industry consolidation, which is impacting the show even beyond the fewer exhibitors this year in Las Vegas. GSX is the new branding for the trade show formerly kno...
Several recent terrorist and mass violence attacks have been directed at soft targets, or relatively unprotected locations where people gather such as outside a music venue or in the unscreened passenger areas at airports. Attacks in public areas have led to the development of new security technologies aimed at protecting soft targets. One company addressing the challenges is Evolv Technology and its Edge automated high-speed personnel screening solution. The system integrates walkthrough fire...
Protecting power grids is essential to deliver electricity that serves millions of consumers. Transmission substations are a component of the power infrastructure that presents unique security challenges. These important facilities often sit out in the open, in remote locations, and were historically protected by little more than cameras or chain-link fences. Much of the current concern about securing electrical substations in the United States originated in response to a 2013 sniper attack, us...
The new Pokemon Go video game, which has taken the world by storm, combines real-world landmarks and locations with virtual creatures in a smart phone video game that requires players to walk around in the real world to “find” the imaginary creatures. It’s a little like what the security industry has been trying to do for years: To achieve convergence of physical and cyber worlds. Pokemon Go security risks To be sure, the new game has presented its own set of security chall...
Security vigilance can be sporadic at many companies and institutions. Facilities tend to tighten security in the days after a scary event happens or makes headlines, and people are generally tolerant of the associated inconvenience – for a time. But as memory fades, so too does tolerance for being inconvenienced. We want to be safe, but we also don’t want to be bothered. We want a security system that both provides safety and is unobtrusive. Security doesn’t have to be inconv...
Milestone Systems is closing in on a year since their acquisition by Canon’s European subsidiary in June 2014. Throughout the ownership transition, Milestone has reiterated its commitment to open systems and continued to flourish, building its “ecosystem” alongside other industry partners. At the recent Milestone Integration Platform Symposium (MIPS 2015), I had a chance to chat with Lars Thinggaard, Milestone’s president and CEO, about industry trends and what’s ah...
ObjectVideo shook the industry a few years ago by launching a series of lawsuits against the industry’s big players, claiming infringement of ObjectVideo’s patents on the basic technologies of video analytics. Some of the targeted companies fought back, but in the end most opted to make the issue go away by signing a licensing agreement with ObjectVideo. The latest twist in the story is major video supplier Avigilon’s acquisition of those patents – and of the 19 related...
One system, one card
DownloadEnhancing physical access control using a self-service model
DownloadAligning physical and cyber defence for total protection
DownloadUnderstanding AI-powered video analytics
DownloadHow to implement a physical security strategy with privacy in mind
Download