Retail security - Expert commentary
The Internet of Things (IoT) is having a significant and ever-changing impact on the way we view video security. Today, cameras are expected to be so much more than devices with which to simply capture images; they need to be far smarter than that. These future-facing cameras are becoming an integral part of the vast digital connectivity infrastructure, delivering a parallel performance as intelligent sensors with the ability to extract the kind of invaluable data that helps businesses make impr...
Small business owners work hard. They are often the first ones there in the morning and the last to leave at night. Even then, they likely bring their work home with them. During that time, everything they do is aimed at making their business as successful as possible. Because of this, many business owners don’t take vacations, and if they do, they spend a lot of time worrying about their business while they’re away. In both cases, the potential for burnout is tremendously high. Th...
Video surveillance as a service (VSaaS) is not just for commercial organisations. Federal, state and local governments can also realise benefits from the technology—and use it to deliver an integrated video surveillance system that addresses some of their unique security needs. Video Surveillance as a Service (VSaaS) What is VSaaS? Simply stated, it’s a cloud-based video surveillance solution that is packaged and delivered as a service over the internet. The price varies depending...
The security industry remains interested in capturing actionable data from video analytics and this year we saw increasing interest from non-security industries. While still a relatively young industry for our market—think of where Google was with collecting metadata 10 years ago—video security works with similar algorithms for capturing various scenarios. The data this provides is becoming more valuable not only for security purposes, but also for business operations, such as deter...
An increase in spending on security, more focus on data security, higher demand for integrated solutions, and steady progress to move beyond the pixel race were key trends in 2017. As we look forward to 2018, we will continue to see development in these areas as well as greater impact of the Internet of Things (IoT) on the video security market. Potential of video security data More and more, users are realising that the real issues in video security are not about pixel counts. Managing incre...
News of cyberattacks seems constant these days. Recently, Equifax, a US-based consumer credit reporting agency, announced that a private customer data breach impacted 143 million people. Earlier this year, 1.5 million connected cameras around the world were hijacked in an unprecedented DDoS attack. As cyber-attacks become more rampant, it’s hardly surprising that governments are stepping in to hold organisations more accountable. One of the most recent examples of this is the European Un...
As a grocery store or supermarket owner, it is very hard to fight theft. Shoplifting and retail theft may not seem like a major deal, but to the small business fighting for survival, it has a big impact on the bottom line. A disadvantage of traditional tools for fighting shoplifting is that they are most effective when the shoplifter is caught red-handed. Once the shoplifter has concealed the stolen product in his or her clothing or bag, it is very hard to see whet...
The smart home market has seen significant growth since 2010. Specifically, less than 0.5% of homes in the American region had connected home devices such as thermostats, lighting, security and entertainment in 2010; by the end of 2017, nearly 12% of households in the region will have connected home devices, an average of six devices per home. The success of smart homes started with professional security providers offering bundled packages, focused mostly on security monitoring. However, due to...
Nowadays, there is a lot of hype around data and its utility for almost any industry – from security and law enforcement to business operations and retail. While we are inundated with information about data and its significance to business success, technological development and fulfilling the promise of the Internet of Things, we don’t always get practical feedback as to how to obtain this valuable data from the resources available to us. Security teams feel this challenge acutely....
Robots have been in the spotlight lately, as tycoons like Elon Musk discuss the perils of automation and artificial intelligence (AI), and roving robots meet their watery demise. These recent events have unmasked a particularly interesting topic: The value of robots in the broader sense, especially as a security tool. The emergence of robotics, automation and AI is not new, but the ongoing discussion about how best to use these continues to fuel critics and supporters alike. Seattle-Tacoma Inte...
With 60 percent of all of the world’s data expected to be created and managed by enterprises by 2025 according to IDC, it’s not surprising to learn that enterprise players have moved swiftly to help their customers and organisations maximise the opportunity around this massive data growth. However, when it comes to one of the most significant drivers of this growth in information—surveillance data— many enterprises struggle to understand how they can apply it to do more...
Since the introduction of smartphones with downloadable applications, vendors have been trying to replace the traditional plastic identification (ID) card with a mobile phone application. People might lose or misplace an ID card, but most people immediately recognise if they are without their mobile phone. Mobile ID badges for access control Bluetooth Low Energy iBeacon technology Technical challenges of mobile ID apps The logical extension is to replace or augment the traditional corpor...
Today's threat landscape is bigger and more broad than ever before, with an increasing number of emerging risks falling on the shoulders of security professionals in a variety of markets. Many of these leaders face the growing concerns of finding efficient, integrated solutions that provide protection from threats, but also can be used in everyday communications to streamline operations, provide access control, and automate workflow. One way today's enterprise organisations, citie...
2016 was a year of fast-paced changes in the market for video surveillance, especially for higher-resolution and panoramic cameras. We spoke with Scott Schafer, Arecont Vision’s Executive Vice President, for his thoughts on 2016 and the year ahead. SourceSecurity.com: Did your predictions for 2016 match up with what you thought back at the end of 2015? How has the intervening year changed the thoughts? Scott Schafer: Looking back on our predictions for industry trends...
Pressure from online shopping is making it even more critical for brick and mortar stores to maximise the revenue per visit Analytics is trending hot for both video and data. The problem for many security video acquisition products is the old adage: bad data in, results in bad data output. The acquisition device has to be able to deliver on the promise to the end user and perform in challenging environments. What products, with what capabilities, are changing the video a...
The holiday season generates 34% of annual sales for retailers but accounts for 37% of annual losses It is that time a year again, when shoppers and shoplifters converge on our retail outlets looking for that all important deal or steal. Peak shopping season This year, the National Retail Federation estimates holiday spending will rise 3.6% from 2015 to more than $655 billion. While the peak shopping season used to be defined as the time between Thanksgiving and Christmas Ev...
Currently some retailers operate two separate speaker systems in their stores: one for broadcasting background music and one for announcements Twenty years ago, IP network cameras launched a revolution in video surveillance. Today, network audio systems are about to do the same for the speaker market. Back in 1996, the predominant video cameras were analogue. They weren’t intelligent. They required an expensive and complex head-end of recording and monitoring systems....
The unfortunate reality in today’s world is that everyday places in our communities that were once thought of as safe – hospitals, schools, shopping malls and office buildings – are now places where people are at an increased risk for being injured by gun violence. Increase in gun violence Shocking incidents of active shootings have become all too common where we work, learn, relax and recuperate. In the wake of the Orlando Pulse shooting, it’s hard to forget that...
PSIM systems extend their value beyond emergencies by including routinemanagement tools, that provide value during daily operations, such as automatingmaintenance activities Physical Security Information Management (PSIM), an acronym termed to describe a family of software platforms that claim to replace traditional command and control (C&C) systems, primarily used to provide situation awareness in control and monitoring centres of Critical Facilities. Traditional C...
As the technology in omnidirectional cameras continues to improve, they are becoming increasingly more affordable to a wider segment of the video surveillance market Just a few years ago, omnidirectional cameras were a novelty. Today, however, this technology has taken the leap to the mainstream. Think about how ubiquitous Google’s Street View is, and you can gain a better idea of the power of omnidirectional cameras. Even consumers are starting to see many forms of omn...
Secure payment card technology at the point of sale and a strong authentication are effective defences against data security threats Data security is one of the top concerns to a retailer’s reputation and its customers’ privacy. The fall-out can be catastrophic, and organisations must understand the threat and take all necessary steps to protect their assets and customers. The challenge has become more complex with the explosive growth in mobile device usage throug...
Soft targets are civilian-centric places suchas churches and retail centres, where securityis not as fortified The terror attack on Paris on Nov. 13 lasted just 23 minutes. The bombers and gunmen split up and attacked seven sites: the soccer stadium where it all began, four restaurants, a bar and a concert venue. All told, they killed 130 people and injured 368 in the time it takes for a coffee break. This situation has raised questions about the security management for conce...
Successful video infrastructure management requires visibility into the network’s behaviour The importance of video in an organisation has been growing over the past several years, almost exponentially. In retail, video images can help detect or deter theft by employees and patrons. Casinos use video partly due to state regulations, to ensure gaming activity is free of deceit or fraud. Branch offices use video to communicate with the head office. Schools use video for di...
This article by Keith Jernigan Sr., General Manager - MOBOTIX Corporation states the enormous impact of smart surveillance on various sectors. Highlighting the changing trends of video surveillance, Keith talks about the several benefits of IoT. He mentions that the new era will see video surveillance companies as more than just video security cameras sellers. To summarise, IoT is forecasted to conjure up businesses offerings, reduce costs and hazards, create jobs and opportunities, thus leading...
When it comes to protecting buildings and property, traditional methods of security—such as structural barriers, security guards, and security cameras—have their limitations. Advanced laser scanning technology can overcome many of these limitations and provide a safe, reliable, and easy-to-use solution. Overview of laser scanning technology Laser scanning technology for building security applications utilises the time-of-flight method, in which a sensor em...
When video analytics first emerged in the security industry about a decade ago, there were high hopes it would instantly transform the landscape of video surveillance. Problem was, the technology was not mature and, in essence, was oversold as far as its capabilities. Analytics such as heat mapping, directional and license plate recognition technology have improved, lending themselves to applications beyond security and into the realm of actionable business intelligence Integra...
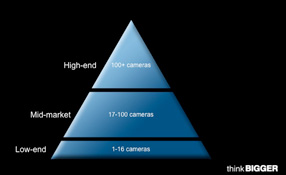
See bigger image Old pyramid w # of cams It’s clear that the network-based physical security industry has matured rapidly over the past few years. As the technology and other components of security solutions have advanced, so too have the customer’s expectations. Security solution companies must evolve in order to meet these new expectations. This requires an understanding of both the technology and the customers’ motivators, issues and hot buttons. Arr...
Employees are the front line of defence — as well as the most economical defence — against shrinkage losses The financial cost of retail shrinkage is huge. The latest Annual Shrink Report issued by Dr. Richard Hollinger and Dr. Read Hayes at the University of Florida puts the total at $36 billion annually. Shrinkage has several causes: customers shoplifting , employee theft, supplier fraud and administrative errors. Frequent inventories and accounting audits coun...
Audio systems can enhance liability protection. Recently, a large regional convenience store chain with units across the Midwest and South supplemented its video surveillance security system with an audio monitoring system. Retail stores with Louroe audio system: The technology has been installed in more than 700 of the convenience retailer’s locations. The Louroe Electronics systems feature omni-directional capability and sensitivity and pick up sound within a 15-foot...
Companies need to increase the knowledge within their business on the range of cyber-vulnerabilities At one time, embedded devices, such as access control components communicating with application software, used proprietary protocols like RS485. Use of proprietary protocols kept these devices safe from attack. However, in this article TDSi Technical Director Mike Sussman explains that the growth of the Internet of Things (IoT) involves a move toward IP-based systems and open s...




























_286x175.jpg)









