India News
Many end-users shell out the cash to acquire the newest high-end devices, plug in, and expect to be wowed A well-developed surveillance system can give a single security guard the power to see what otherwise might take a hundred pairs of eyes to see. But what happens when all the components are all connected and powered up, and the resulting image on the screen is, well, indiscernible, or, at the very least, terribly pixelated? Many end-users shell out the cash to acquire the...
The 62nd ASIS International Seminar and Exhibits will run from September 12 to September 15 in Orlando, Florida. ASIS estimates that the Seminar may attract more than 20,000 security professionals to the Orlando Convention Center, where the event is being held. Giving back to the host community The Seminar always has a major economic effect on the host community. This year, ASIS will inaugurate a programme called Security Week, which is designed to give something back to the Sem...
Winning full engagement from your prospects is tougher today than ever before thanks to the Internet For months, maybe years, you’ve worked to secure an appointment with a prospective customer. You’ve utilised your network, and shown persistence. You’ve consulted with your boss, brainstormed with your peers, and even asked for advice from your friends. You’ve given it every ounce of energy you have, and finally… finally, the...
There’s no better indication that robots are the next big thing in security than the formation of the industry organisation known as Robolliance. It’s billed as “a forum for technology partners and industry experts in robotics, surveillance and security to advance the understanding and awareness of the Autonomous Robotics marketplace.” Founded by Sharp Electronics Corp, its members include some of the biggest names in security and technology including Bell and Howell, R...
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) in the United States fosters health insurance coverage for workers and their families, and requires national standards for electronic health care transactions. The law’s privacy provisions include protection of information related to any individual’s health status, provision of health care, or payment for health care. There are also additional health privacy laws specific to California. Inter...
Sometimes you see it coming and want to scream out: “Don’t do that.” We all make mistakes, but it’s hard to sit and watch others as they go down the wrong path. It’s especially difficult when the errant party is a customer, and when their wrong move might somehow end up reflecting badly on you as a technology or security systems provider. Much better to anticipate the problem by expecting the possible mistake before it happens. We asked this week’s Expert Pane...
What's the White Paper about? The mobile industry is known as one of the most innovative and fast-paced and what we have seen in recent years has been nothing short of remarkable. This rapid growth is affecting the underlying technologies and standards in mobile devices as more people use their devices in their daily life and new applications are developed. This white paper from HID Global explores the essential elements in successfully implementing mobile access, fr...
Temperatures ranging between -40°C and -5°C, storm wind speeds of more than 100 km/h, constant daylight during summer and darkness during winter. This must be Antarctica. This is where the Belgian Princess Elisabeth Antarctic base is situated, the first "zero emission" polar research station which was designed, built and operated by the International Polar Foundation (IPF). Since the station went into service on February 15, 2009, it has been already hosting a multiple of scientific pro...
Today, we find ourselves in a world where we all need to talk less about products and more about solutions The security industry has changed a lot in recent years. Many will remember a time not so long ago when it was about buying boxes/pieces of tin, opening them up and installing them. Today, we find ourselves in a world where we all need to talk less about products and more about solutions. Despite this, there is still an inclination to put everything in a ‘box’...
SALTO’s BLE enabled access control increases efficiency and convenience for end users in any vertical SALTO Systems, a manufacturer of electronic access control solutions, will showcase its latest security innovations — including new BLE enabled products — at the annual ASIS International Conference to be held in Orlando, Sept. 12th-15th. Bluetooth Low Energy (BLE) technology “SALTO’s emphasis on incorporating mobile access Bluetooth Low Energy...
Qognify will be demonstrating its multi-award winning solutions in booth 3451 at ASIS International 2016 Qognify, formerly NICE Security, will showcase its portfolio at ASIS International in Orlando Florida, September 12th-14th. With significant advancements to its security portfolio, Qognify will be demonstrating its multi-award winning solutions in booth 3451. VisionHub VMS The new next-generation, web-based VisionHub is the winner of the Security Industry Associati...
Matrix will showcase its range of Biometric Access Control and IP video surveillance solutions Matrix, a manufacturer of telecom and security solutions, is participating in ASIS 2016, from 12th – 15th September 2016. Matrix will showcase its well-engineered security solutions specifically designed for enterprises. Biometric access control At ASIS 2016, Matrix will showcase its range of Biometric Access Control solution and its advanced applications. Mobile being...
IT access control offers significant cost savings per unit or door as less hardware is required to cover a large area Over the last several years, there has been a revolution in access control methodologies including increased integration with video management software and video surveillance capabilities that better protect businesses and enterprise applications. But nowhere is the integration space more progressive in scope than the collaboration between the IT department and...
Distributors have traditionally played an important role in the physical security market, ensuring ready availability of products that systems integrators need to complete their projects. But a changing industry has had dramatic impact all along the supply chain of which distributors are a critical link. We asked this week’s Expert Panel Roundtable: How is the role of distributors changing in the market, and what is the impact?
Creating and accessing intelligence is increasingly part of the mission of corporate security departments, and of Safe Cities applications. Such capabilities were previously the domain of military and government applications, but the same approaches used to provide intelligence from military bases can also be applied to Safe Cities and corporate security projects. Edge360 is a six-year-old company with roots in the military and Department of Defence surveillance. Now, Edge360 is looking to app...
Dennis Sage Home Entertainment, Phoenix, is a best-in-breed audiovisual contracting services firm that gradually began expanding its offerings to security several years ago. After testing the waters, hiring experienced technicians and learning about the parallels with its current business, the company made a successful transition. Now, Dennis Sage, President and Chief Executive Officer (CEO), is also counting on heightened customer engagement and stickier clients as he moves into the role of t...
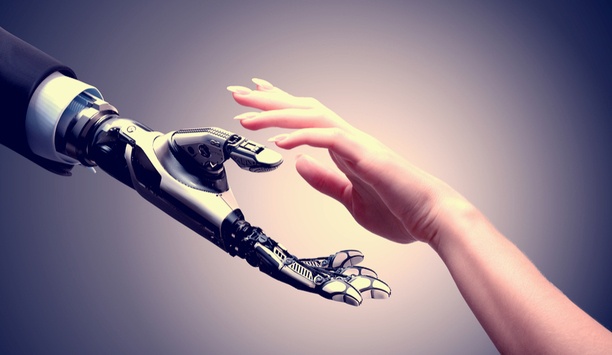
(Image credit: Antonio Scorza / Shutterstock.com) The era of the “killer robot” hasn’t arrived, exactly, but it may not be far off. Police and the military have been using these machines for decades now to disarm bombs and provide reconnaissance in areas where it would be risky to send officers or soldiers. When Dallas Police equipped a robot with an explosive device and sent it in to take out a sniper who had killed five officers, it raised eyebrows and conjured images of a...
A lot has changed in the last 15 plus years in the security industry, including the ability to process and analyse Big Data. The growth rate of data has reached an astounding pace. Today, best estimates are that about 2.5 quintillion bytes of data are produced every day—that’s 2.5 followed by a staggering 18 zeros! The volume of data feeding into businesses is so vast, the only means available to leverage this data to drive decision making is to harness the power of a Business I...
The security industry as a whole is migrating from the historical mechanical lock to the newest technology of electronic locks Mechanical locks and keys date back thousands of years and have undergone many changes, but the industry’s transition to electronic locks might be the most important, lasting, and surprisingly affordable security and safety change of all. The objective behind the creation of locks so long ago remains: to control a value on the other side...
IFSEC Southeast Asia 2016 is an opportunity to create new networks with leading companies and peers The region’s security, fire and safety industry is getting excited for the fourth edition of IFSEC Southeast Asia 2016. On 7th - 9th September 2016, industry experts from around Southeast Asia will gather on the show floor to build networks amongst industry peers, discuss on the future development and business deals, and obtain new information from seminars. All these will...
The need for security convergence and shared threat intelligence is markedly increasing “Converged security” has been a buzz phrase for more than a decade, but the industry is just now starting to reap the rewards. Converged security recognises that truly comprehensive organisational risk management involves the integration of two distinct security functions that have largely been siloed in the past: information security (network operations centre or NOC) and physi...
Part 8 of our healthcare series Hospitals are challenging environments. A hospital requires oversight 24 hours a day, seven days a week Access control in particular has advanced significantly to offer healthcare facilities the ability to control access remotely, through mobile applications, confirm identity quickly and easily and program varying levels of access for visitors, patients, doctors and staff. Hospitals are challenging environments. A hospital requires ov...
It’s become a hot topic lately, but what are the real prospects for the smart home and home automation market? More specifically, what role can the security industry play in what is seen as a growth area? Earlier this year, IFSEC International in London saw the launch of a new home automation zone featuring a replica smart home, showcasing a range of interconnected devices such as intruder alarms, CCTV, biometric readers, door entry solutions and locks, as well as wireless control of bli...
Sometimes customers expect more out of a security system. A brand new security system just doesn’t perform as the customer expected it would. In fact, one might argue that the many variables in today’s complex systems make it more likely than ever that some element of a system might not measure up to a customer’s expectations. What happens then? We asked this week’s Expert Panel Roundtable: What happens if a customer’s expectations of system performance are greater...
Part 2 of our robots in security series Companies realised they could improve security by mounting laser sensors and cameras on a mobile platform such as Knightscope's Autonomous Data Machines Security and safety robotics, unlike any other industry, is driven by customer and market demand. Once buyers acquire robots, they often find new things they want them to do. Manufacturers are then called upon to respond to those demands, and they often do. Enhancing security...
All ASUSTOR NAS devices are compatible with Seagate’s IronWolf 10 TB hard disks, 6 TB Enterprise NAS hard disks & 10 TB Enterprise Capacity hard disks ASUSTOR, a provider of network storage solutions, has announced today that, after stringent testing, all of its NAS products are fully compatible with Seagate’s newly launched IronWolf 10 TB NAS hard disks, 6 TB Enterprise NAS hard disks and 10 TB Enterprise Capacity hard disks. These hard disks are recommended...
TDSi will be giving visitors a chance to see its new range of GARDiS software and hardware solutions Integrated security manufacturer TDSi will be giving visitors a chance to see its new range of GARDiS software and hardware solutions at IFSEC Southeast Asia 2016, which is being held in Kuala Lumpur from 7th-9th September. The show follows this year’s highly successful IFSEC International in London, which saw increased stand visitor numbers and considerable interest in t...
PROMISE Technology's VTrak solution is an instrumental part of the city surveillance project in Singapore Singapore is one of the most densely populated regions in the world, with over 7,000 people per squared kilometre crammed into the island country. A natural issue that arises with so many people in such a small area is that legally parking one’s car is not an easy task. Illegal parking is a real problem in Singapore and it affects the safety and convenience of Singap...
Iris ID’s non-contact solution provides highly accurate identification using the iris to authenticate employees Iris ID, a provider of iris biometric technology, has announced its IrisAccess® iCAM7000 identity authentication system has been installed for employee time and attendance at all Sharjah Co-Operative Society retail stores in the United Arab Emirates. The retailer operates 26 stores with more than 3,000 employees throughout Sharjah, a UAE state, and the cap...
For the past several years, information technology security concerns and priority regarding insider threats have steadily risen as evidenced by a variety of surveys across the IT security industry. Companies are becoming increasingly worried about insider threats. From the cyber security perspective, insider threat is primarily focused on malicious threats to the company either by, or to, information technology assets. Whether it is fraud, intellectual property theft, or ev...
Browse security news
Featured products
Related videos
Find Lost Wallet with Dahua WizSeek
Dahua Traffic Signal Controller Highlight
CLIQ Connect
One system, one card
DownloadEnhancing physical access control using a self-service model
DownloadAligning physical and cyber defence for total protection
DownloadUnderstanding AI-powered video analytics
DownloadHow to implement a physical security strategy with privacy in mind
Download- India Security companies
- India Manufacturers
- India Distributors
- India Resellers / Dealers / Reps
- India Installers
- India Consultants
- India Systems integrators
- India Events / Training / Services
- India Manned guarding
- India Training organisations
- India Associations / regulatory bodies
- India Event organisers
- India Media
- India Recruitment / personnel
- India Services