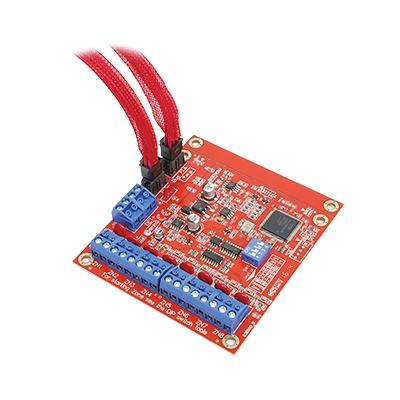
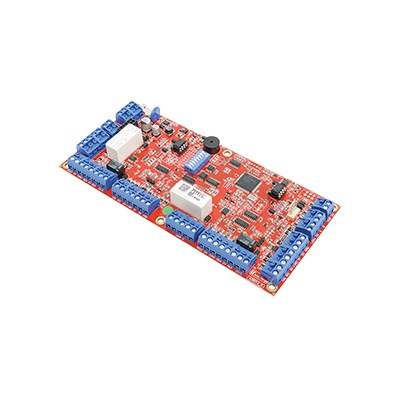
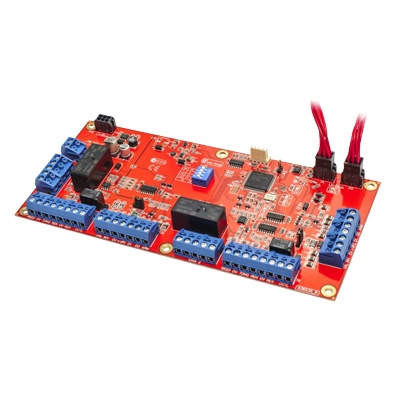
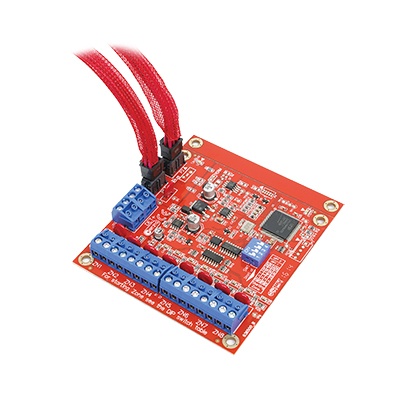
Inner Range 995086 Access control system
Technical Specification
- Make: Inner Range
- Model code: 995086
- Series: Concept 3000 / Access 4000 Series
- No/ Type of Inputs/ Outputs: 8 inputs / 8 outputs
- Operating Temperature oC: 0 ~ +40
The mini expander module can be used within the same Concept 3000 or IR Access 4000 applications as the 16 zone universal expander, providing a cost effective solution whenever a small number of zones and auxiliaries are required. It has a programmable de-bounce feature for increased sensitivity to inputs such as hold-up buttons, event counting and monitoring of electronic plant equipment. The input counting feature enables accurate monitoring of events or customer activity.
Read more| Make | Inner Range |
|---|---|
| Manufacturer | Inner Range |
| Category | Access Control>Access control systems & kits |
| Model code | 995086 |
| Series | Concept 3000 / Access 4000 Series |
| No/ Type of Inputs/ Outputs | 8 inputs / 8 outputs |
| Environmental Specifications | Operating Temperature oC: 0 ~ +40 |
| Electrical Specifications | Voltage: 11 ~ 14 |
| Physical Specifications | Dimensions mm: 325 x 250 x 112 |
| Accessories | Mini Expander Module |
| Additional info | The mini expander module can be used within the same Concept 3000 or IR Access 4000 applications as the 16 zone universal expander, providing a cost effective solution whenever a small number of zones and auxiliaries are required. It has a programmable de-bounce feature for increased sensitivity to inputs such as hold-up buttons, event counting and monitoring of electronic plant equipment. The input counting feature enables accurate monitoring of events or customer activity. |
You might be interested in these products
Related Whitepapers
Beyond security: access control for multi-tenant sites
The power of integration in physical security systems
IoT connectivity
One system, one card
DownloadAligning physical and cyber defence for total protection
DownloadUnderstanding AI-powered video analytics
DownloadEnhancing physical access control using a self-service model
DownloadHow to implement a physical security strategy with privacy in mind
Download