Honeywell Security TVC-2100 CCTV software
Technical Specification
- Make: Honeywell Security
- Model code: TVC-2100
- Accessories: ATM Video Text Inserter
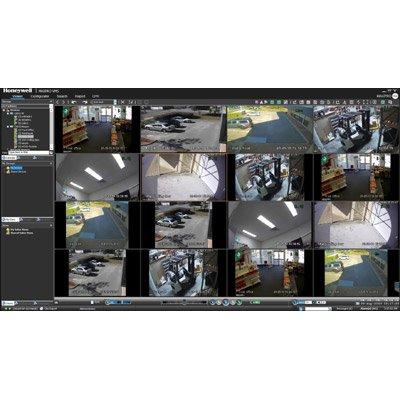
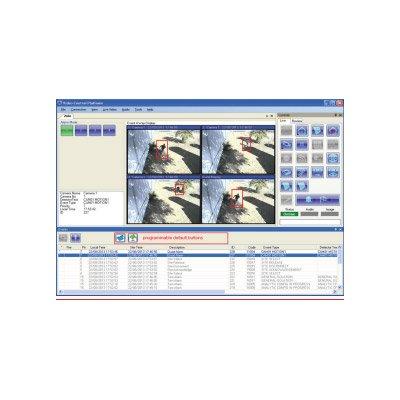
The TVC-2100 Series text inserter is designed to communicate with 4 to 10 register interfaces. It superimposes transaction information onto corresponding video of the cashier on a one register per channel basis. The TVC-2100 Series text inserter is installed between the cameras and the video processor; therefore, it can be used with multiplexers, quads, etc. The composite image with the text overlay can be viewed live or reviewed later from a video recorder. Questionable transactions such as VOID and NO SALE can be reviewed in minutes when the alarm features of the TVC-2100 Series are used to trigger the alarm inputs of the video processor.
Read more| Make | Honeywell Security |
|---|---|
| Manufacturer | Honeywell |
| Category | CCTV>CCTV software |
| Model code | TVC-2100 |
| Accessories | ATM Video Text Inserter |
| Additional info |
The TVC-2100 Series text inserter is designed to communicate with 4 to 10 register interfaces. It superimposes transaction information onto corresponding video of the cashier on a one register per channel basis. The TVC-2100 Series text inserter is installed between the cameras and the video processor; therefore, it can be used with multiplexers, quads, etc. The composite image with the text overlay can be viewed live or reviewed later from a video recorder. Questionable transactions such as VOID and NO SALE can be reviewed in minutes when the alarm features of the TVC-2100 Series are used to trigger the alarm inputs of the video processor.
|
You might be interested in these products
Related Whitepapers
Nine ways to make your retail security system work harder
The benefits of Edge AI + Cloud for security systems
Video technology: making cities safer & improving lives
One system, one card
DownloadAligning physical and cyber defence for total protection
DownloadUnderstanding AI-powered video analytics
DownloadEnhancing physical access control using a self-service model
DownloadHow to implement a physical security strategy with privacy in mind
Download