Video surveillance - Expert commentary
Affiliated Monitoring’s UL-Listed monitoring centre with a second floor dedicated to areas for security company meetings Central monitoring stations have innovative approaches to assist security installing companies in growing their account base, adding value and boosting recurring monthly revenue (RMR). These companies do much more than simply monitor accounts – today they provide a host of services to give security installing companies the added edge in an extrem...
For police, BWCs can significantly improve how evidence is collected by recording the visual and audio actions Body worn cameras (BWCs) are becoming common place in law enforcement. While the spotlight for body cameras is on police in the news, BWCs are also sought after in security-related contracts for airports, campuses, correctional facilities and for private security. It’s quite likely interactions with police or security guards will be recorded (people who re...
When video analytics first emerged in the security industry about a decade ago, there were high hopes it would instantly transform the landscape of video surveillance. Problem was, the technology was not mature and, in essence, was oversold as far as its capabilities. Analytics such as heat mapping, directional and license plate recognition technology have improved, lending themselves to applications beyond security and into the realm of actionable business intelligence Integra...
ESA opens the 2015 exhibit show floor with a ribbon cutting ceremony The Electronic Security Association (ESA) wrapped up ESX 2015, June 24 to 26 in Baltimore, Md., drawing integrators, manufacturers and association members from across the country to attend the annual educational, exhibits and networking event. Security integration companies Celebrating its eighth year, the show is jointly owned and sponsored by ESA and the Central Station Alarm Association (CSAA). ESX inclu...
Potential deployments of video analytics, or my own preferred term “intelligent scene analysis,” are being worked on by some of the best minds at university campuses across the United Kingdom. Later this year I will visit Kingston University whose Digital Imaging Research Centre is one of the largest computer vision groups in Europe. Violence prevention through analytical intelligence Here, I talk to Prof David Marshall of Cardiff University, who describes work...
The deputy commissioner spoke about trends and budgeting to MBA students at Cass Business School One of the main challenges for senior officers in London’s Metropolitan Police Service is to develop policing techniques that reflect changing demographics. The main demands on an officer’s time are complex cases, often involving child protection and requiring interaction with other organisations such as health services. Missing persons' cases can now be extremely compl...
Today, a number of school districts are saying no to these kinds of realistic active shooter drills In the wake of the shootings at Columbine High School in 1999 — 16 years ago — and the school shootings that have followed, we have struggled to figure out how to keep students and teachers safe during such an attack. Protective measures An approach to the problem that has grown controversial is armed assailant or active shooter drills. Six states including Arkansa...
Just how big is the home automation industry? One way to tell is by looking at the sheer number of companies – large and small—that have rushed to enter this fast-growing space. They include some of the world’s largest corporations – Apple and Google – along with the nation’s biggest cable and telecom companies – Comcast and AT&T. It includes big names in security like Honeywell and ADT. Then there are less known, but fast growing, contenders such as...
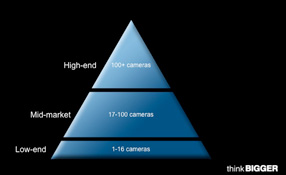
See bigger image Old pyramid w # of cams It’s clear that the network-based physical security industry has matured rapidly over the past few years. As the technology and other components of security solutions have advanced, so too have the customer’s expectations. Security solution companies must evolve in order to meet these new expectations. This requires an understanding of both the technology and the customers’ motivators, issues and hot buttons. Arr...
The great increase in the amount of data is driving physical security to the cloud Physical security is migrating to the cloud — because it improves the performance of physical security technology while holding down costs. “Essentially what is happening is that physical security technologies are growing more powerful and generating more and more data,” says Steve Surfaro, business development manager and security industry liaison with Axis Communications, wh...
When asking exhibitors at IFSEC International 2015 about what drives their markets, many cite system integration as a key factor. And they want more of it. Integration as business “driving force” For example, John Davies of TDSI says customers are now seeking out system integration. “They want a solution rather than components, such as linking access control with building management systems or with an organisation’s IT network to control access to its computers,”...
Although in many cases CCTV has been an effective investigation tool, its full potential is not being realised It’s all very well installing CCTV cameras, but to be effective users have to know what to do to make images available to the police and courts, according to detective chief inspector Mick Neville of the Metropolitan Police. Although in many cases CCTV has been an effective investigation tool, its full potential is not being realised, says Neville, who is due t...
This year's IFSEC International show in London will provide a reflection of the physical security industry's rapid growth, especially in the video sector, says one industry observer who is also a speaker at the show, coming up 16-18 June. “If we look at the overall trend, it is no surprise to anyone that IP is driving the growth and the future of the security business,” says Jim McHale, managing director of research company Memoori, and a speaker at IFSEC. Secur...
Security is a big concern for local government buildings, but there are measures that can make a difference Back in August of 2013, Rockne Warren Newell, armed with a rifle and a handgun, stormed a township meeting in the Ross Township Municipal Building in Saylorsburg, Pa. Witnesses say he fired through a wall into the meeting room and then burst into the room itself, guns blazing. Three people died, and two sustained wounds before citizens attending the meeting restrained hi...
Organisations are looking for ways to maximise resources and extract value from video security investment "There’s valuable information hiding within surveillance video. Extracting it can make a security department more efficient and provide a clear return on investment to their organisation." - Dror Irani, CEO and President, BriefCam - The Video Synopsis company. Challenges of video surveillance Video surveillance systems are a blessing to security. They are also a cu...
Managed and hosted services allow users access from a variety of connected devices It’s not about hardware anymore, although quality components are a must. Now, it’s about how technology performs. For the systems integrator, there’s also an opportunity to provide essential services to keep customers connected. As with many other businesses, the security industry is being “disrupted” and influenced by the cloud. Delivering outsourced security and...
The future will produce cost-effective solutions that can provide meaningful coverage of wide expansive areas The greatest trend in history will continue to change the world, and the physical security market. It’s called Moore’s Law. In accordance with Moore’s Law, our electronics have consistently doubled in speed, halved in size, or halved in price every two years for decades already. This trend means that our electronics, communications networks, data ne...
Strategic management of costs is important when considering video storage systems Costs are at issue when considering any component of a video system. Strategic management of costs is especially important when considering video storage systems because storage accounts for such a large cost component of networked systems. Gartner’s Total Cost of Ownership (TCO) As enterprise products begin to dominate the video storage market, more attention needs to be addressed to Gar...
Integrators and end users should be aware that their definition of open might differ from those of security manufacturers Much of the buzz in the industry today about open architecture is driven by the IT world, with many security-related decisions now falling on an organisation’s IT department, where true open architecture has been around for a long time. Closed systems like we’ve experienced in the security world are not just viewed as foreign to the IT world; th...
Not too long ago the idea of home automation was strictly the province of the rich and famous. With costs that soared as high as $100,000 or more, controlling HVAC, lighting, doors and security from a single source just wasn’t in the budget for Main Street America. That was then, but now is an entirely different story. The “connected home” in which smart phones and tablets serve as controllers for Internet-enabled devices has gone mainstream. Installers are still fashioning hi...
The fundamental value of data is widely apparent in modern society, and its loss may have significant consequences Video data is critical to today’s enterprise. The latest video storage systems must offer dependable operation that doesn’t risk loss of that critical data. DDN - When performance matters “Not only is bandwidth very important, but functionality cannot be lost when a storage system is having a bad day,” says Jeff Adams, director of sales,...
According IHS Technology, more than 11 million consumer and DIY network cameras will be shipped worldwide this year Perhaps we should start looking at do-it-yourself (DIY) systems such Google’s Nest and other devices as an opportunity for existing security contractors – those that are open-minded anyway – to bring in additional customers and new streams of recurring monthly revenue (RMR). DIY systems continue to proliferate in the marketplace and are availab...
Most of us have a basic instinct as to what is and is not ethical behaviour. But is instinct enough? “Ethics and the security industry is a balancing act,” says Mike Hurst, vice chairman of the UK Chapter of ASIS International. “Most people will have an instinct as to what ethical behaviour is, but there’s an absence of hard and fast rules.” Examples often crop up in video surveillance situations, Hurst says. For instance, when and where i...
SWOT evaluates a company’s Strengths, Weaknesses, Opportunities and Threats (SWOT) in connection with a project Expanding into other countries with sales offices, manufacturing facilities and distribution centres can present a number of security risks. SWOT analysis for security strategy Physical security technology can help to mitigate some of these risks. “The physical security technology used in international locations is similar to what we use here, but t...
The trend towards greater unification is facilitated by an all-encompassing shift to IP technologies As more organisations are looking for ways to maximise resources and increase operational efficiencies, unification of multiple security and business systems is gaining popularity. From the central command center, there is significant time lost when operators have to jump from video surveillance to access control systems to analyse an incident and take appropriate measures. Eve...
Maricopa County installed a fully integrated security controls system, featuring a VMS Larger IP video systems require plenty of storage, and several high-profile applications help to demonstrate the value of storage in today’s networked video environment. Maricopa county security project One example is the Maricopa County (Ariz.) Sheriff’s Office, which is nationally recognised for its zero tolerance toward crime and unwavering focus on innovation in law enforce...
Since 2006, the LUSAX research program at Lund University in Sweden has investigated the effects of digitisation on the physical security industry. This article will look into the forces driving digitisation, and how those forces broadly translate and impacts the physical security industry. Historically, physical security systems have moved from purely mechanical systems into systems holding both mechanical and electronic low-voltage circuit-based components. Development was...
Honeywell recently helped the Penns Valley Area School district in Pennsylvania design and implement a custom security system Security systems are just part of the solution to protecting primary/secondary schools. Technology can contribute to a broader, holistic approach to security that is customised to meet the needs of each educational institution. Honeywell has helped many schools customise security systems to meet each school’s unique needs, says Bruce Montgomery,...
One key misconception is that solid-state drives (SSDs) are going to replace hard disk drives (HDDs) Like many areas of the security market, the field of digital video storage systems has its share of misconceptions and missed opportunities. We called on manufacturers of these systems to set the record straight. Hard disk drives (HDDs) will continue to rule One key misconception is that solid-state drives (SSDs) are going to replace hard disk drives (HDDs), says Henk Van Den...
Beyond the need to install new systems, often overlooked is how schools are going to pay for security upgrades Limited financial resources are a common pain point for primary/secondary schools looking to implement cutting-edge security technology. But security needs persist despite scarce resources. All school administrators want to do everything in their power to secure their facilities against threats. More schools are recognising the benefits and, in some cases, requiremen...