Cloud security - News
The Nemetschek Group, a pioneering software provider for the AEC/O and media industries, announced the next steps in the go-to-market approach of its solution dTwin. To accelerate the global adoption of Digital Twins, Nemetschek is building a network of partnerships across the world for reality capture, data integration and value consulting. The first partners have been secured in Europe, Asia, Africa and North America. dTwin is Nemetschek’s horizontal, open, and cloud-based digital...
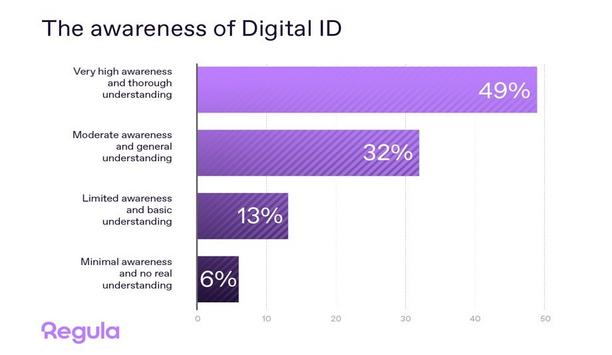
As more countries adopt the concept of digital identity, regulators are keen to showcase their plans and successes. But what do businesses think about this shift? To find out, Regula, a global developer of forensic devices and identity verification (IDV) solutions, commissioned a study to survey companies across different regions and industries to get a sense of their readiness, concerns, and expectations for digital identities. Digital identity Digital identity is considered to be a way to i...
In collaboration with key partner Trinet Technologies Pte Ltd, Anviz organised two successful roadshow events. Both events brought together more than 30 industry experts who showed great enthusiasm for Anviz's business model of user scenario-driven solutions and interest in the new features of the product. Need for Southeast Asian Markets: RCEP Brings New Opportunities, Largest Incremental Market in the World As the largest FTA in the world, which will lead the development of global free trade...
TraiCon Events will be hosting Botswana’s premier cybersecurity event titled “Cyber Revolution Summit” scheduled on 9th August 2024 in Gaborone, Botswana. This summit will feature keynote presentations and panel discussions with top security experts from various industries covering a range of topics, including cybersecurity innovations, data privacy & security, risk management, network security, threat detection & intelligence, and vulnerability management. ...
IDEMIA Public Security North America, the biometrics solutions pioneer for law enforcement agencies, announced that it has implemented its cloud-native, fully functional Automated Biometric Identification System, STORM ABIS, in Volusia County, Florida to support its latent print unit. The Volusia Sheriff’s Office is the first law enforcement agency in the nation implementing a cloud-native ABIS that can search county, state, and federal databases from a single application. Volusia County,...
New data from the latest members’ survey of the ClubCISO community, in collaboration with Telstra Purple, highlight CISOs’ confidence in generative AI in their organisations. Around half of those surveyed (51%), and the largest contingent, 50%) believe these tools are a force for good and act as security enablers. In comparison, only 25% saw generative AI tools as a risk to their organisational security. Risks linked to Gen AI tools The study's findings underscore the proactive st...
Check Point® Software Technologies Ltd., an AI-powered, cloud-delivered cyber security platform provider, has published its Global Threat Index for April 2024. Androxgh0st and LockBit3 attacks In April 2024, researchers revealed a significant increase in the use of Androxgh0st attacks, with the malware being used as a tool for stealing sensitive information using botnets. Meanwhile, LockBit3 remained the most prevalent ransomware group in April, despite a 55% drop in its rate...
Illumio Inc., a Zero Trust Segmentation company, announced it has become a member of the Microsoft Intelligent Security Association (MISA), an ecosystem of independent software vendors (ISV) and managed security service providers (MSSP), who have integrated their solutions with Microsoft security technology to build a better defence against a world of increasing cybersecurity threats. The development follows the release of Illumio for Microsoft Azure Firewall, which combines the security benefi...
The Cyber Safety Force (CSF) has launched to change the way businesses manage their cybersecurity. Forming a consortium of renowned cyber experts, the CSF takes a data-driven, collaborative approach to revolutionise the way businesses think about and manage threat defence and risk aversion – moving from ‘cybersecurity’ to ‘cyber safety’. The CFO recently found that 75% of security professionals have observed an increase in cyber attacks over 2023, with th...
Over three in ten US-based critical infrastructure organisations (36%) that have fallen victim to a ransomware attack have risked legal repercussions by paying a ransom. The findings are in new research by pioneering cybersecurity services firm Bridewell, surveying 519 staff responsible for cybersecurity at US critical infrastructure organisations in sectors such as civil aviation, telecommunications, energy, transport, media, financial services and water supply. Infringing UK and US laws 66%...
A single compromised account can be a gateway for attackers to access confidential data, leading to financial loss, legal consequences, and damage to the company’s reputation. This threat is not limited to any specific platform and affects everything from email accounts to secure business databases. Before exploring strategies for MSPs to mitigate this cyber risk, let’s first understand what an account compromise is, its security impacts, and ways to detect it. What Is a comp...
Cohesity, a pioneer in AI-powered data security and management, announced the appointment of Dr. Craig Martell as Chief Technology Officer. In this role, Dr. Martell will bring his deep industry expertise to shape the company's technical vision, incorporating current and evolving industry and customer trends to define and execute a strategic and impactful roadmap for the company’s future. Digital and AI plan growth Dr. Martell brings extensive industry and public sector experience and u...
Gcore, the global edge AI, cloud, network, and security solutions provider, has announced the launch of a new DDoS protection point of presence (PoP) for its robust global edge network, in Dubai, UAE. The company has more than 30 protection PoPs across six continents, including Europe, Africa, the Americas, and the Middle East. The new Dubai filtering point allows customers to take advantage of advanced DDoS protection services without delay. Dubai PoP By opening the Dubai PoP and expanding i...
Verkada, a pioneer in cloud-based physical security solutions, announced it will offer customers a new AI-powered search in Beta. Leveraging a large language and large vision model, Verkada's AI-powered search will enable customers to use everyday language to search their video security camera footage for people and vehicles, making their investigations even more intuitive and efficient. "Our new AI-powered search is an exciting expansion of the way that Verkada leverages the latest AI and comp...
Exabeam, a global cybersecurity pioneer that delivers AI-driven security operations, announced Investigation Timelines™ within the Exabeam Search™ application, a powerful new capability on the Exabeam Security Operations Platform™. An industry-first, Investigation Timelines break down silos and simplify investigations for security analysts with integrated cross-platform workflows. Designed to empower security teams amid growing threats and skills shortages, this innovative cap...
Allied Universal®, the world’s renowned security and facility services company, has been named to the Newsweek list of America's Greatest Workplaces for Job Starters 2024 with a ranking of four and a half stars. The list was compiled based on responses from people with less than five years of employment experience currently working at companies with more than 500 employees. Greatest Workplaces for Job Starters “Allied Universal is honoured to be recognised as one of Amer...
Google Workspace is a set of productivity applications with over 3 billion users and 10 million paying customers around the world. As the storage of a massive amount of sensitive information, this cloud-based suite is a top security concern for businesses. The risk of data breaches makes it crucial for MSP to implement data loss prevention (DLP) controls to prevent leaks within apps, such as Gmail, Drive, Docs, Sheets, Slides and more. Let’s review how. What is DLP in Google Workspace?...
Milestone Systems, a global pioneer in video technology, is at the forefront of the video security industry, emphasising responsible technology innovation across its operations. The company will host this free, one-day event on May 7 in Toronto. Geared to IT pioneers and security professionals, the day will feature engaging presentations from Milestone's technology partners across key industries such as education, healthcare, city surveillance, and hospitality. Attendees will gain insights into...
Barracuda Networks, Inc., a trusted partner and major provider of cloud-first security solutions, announced that Neal Bradbury has been elevated to the role of Chief Product Officer. In this new role, Neal will lead a unified product, engineering, and advanced technology team to steer the vision for Barracuda’s comprehensive cybersecurity platform and drive customer-centric innovation across the entire portfolio. The platform is designed to protect customers across all attack surfaces inc...
Genetec Inc., a renowned technology provider of unified security, public safety, operations, and business intelligence solutions, announced that its new enterprise-grade SaaS solution, Security Center SaaS, gives organisations the complete freedom to choose the door controllers, cameras, and devices that work best for their business. Based on an open platform architecture, Security Center SaaS enables organisations to connect direct-to-cloud with the latest Axis, Bosch, Hanwha, and i-PRO camera...
In an awards ceremony held at California State University, Fullerton, Allied Universal® Global Chairman and CEO Steve Jones received the 2024 Excellence in Executive Leadership Award from the university’s Giles-O’Malley Centre for Leadership. “I am honoured to be recognised for the innovative strategies Allied Universal has implemented to further the security industry,” Jones said. “Leadership and innovation have always held a steadfast pla...
F5 announced new best-in-class security offerings that strengthen protections and simplify management for customers. With the launches of F5 Distributed Cloud Services Web Application Scanning, BIG-IP Next Web Application Firewall (WAF), and NGINX App Protect for open-source deployments, F5 is extending its leadership with the industry’s most effective and most comprehensive AI-ready app and API security suite. SOAS report The news comes as F5’s just-released 2024 State...
Drata, the pioneering compliance automation platform, announced that it has acquired oak9, a cloud-native security platform, and released a new capability in beta to seamlessly bring continuous compliance into the software development lifecycle. The acquisition positions Drata as the only platform of its kind that monitors compliance both before and after code is deployed to production. This capability, called Compliance as Code, will be demonstrated at RSA, May 6-9 in San Francisco. Cloud-nat...
Global technology solutions provider - Arrow Electronics, Inc. (ARW) announced that Broadcom selected it as the sole provider for its CloudHealth from VMware offering. CloudHealth is designed to help businesses simplify financial management and operations (FinOps) across multi-cloud environments effectively. Arrow Electronics and Broadcom partnership “Arrow is pleased to build upon our strategic relationship with Broadcom by becoming the exclusive provider of the CloudHealth offering,&r...
Aqua Security, the pioneer in cloud-native security, and Orca Security, the pioneer in agentless cloud security, announced a new partnership to deliver best-in-class cloud-native security through a deep integration between their platforms. Joint customers will benefit from the powerful combination of multi-cloud visibility and security provided by the Orca platform combined with multi-and hybrid cloud runtime protection for cloud-native workloads offered by the Aqua platform. Right cloud-...
Illumio, Inc., the Zero Trust Segmentation company, announces its partnership with pioneering cloud security provider Wiz and joins Wiz Integrations (WIN) Platform. Illumio enhances WIN by bringing the power of Illumio’s Zero Trust Segmentation platform to the partner ecosystem, so that customers can seamlessly integrate Wiz into their existing Illumio workflows. Benefits of security findings WIN enables Wiz and Illumio to share prioritised security findings with context including inven...
Honeywell released its 2024 USB Threat Report, which provides new insight into how “silent residency” is an increasing cyber threat for industrial and critical infrastructure facilities. In the report, Honeywell highlighted the growing risk of “living off the land” (“LotL”) attacks in which adversaries use USB devices to gain access to industrial control systems to hide and observe operations before launching attacks that evade detection and manipulate the ta...
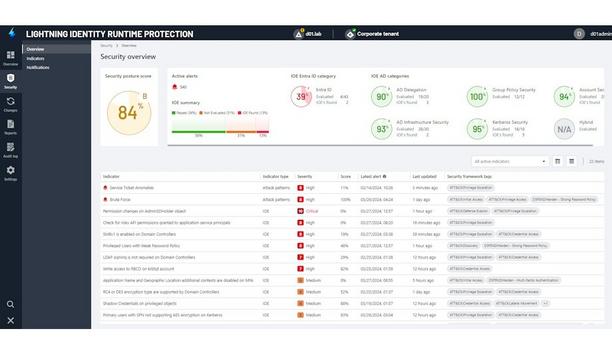
Semperis, a pioneer in identity-driven cyber resilience, announced the release of Lightning Identity Runtime Protection (IRP), a new identity threat detection and response (ITDR) offering that uses machine learning models developed by identity security experts to detect widespread and successful attack patterns such as password spray, credential stuffing, other brute force attacks, and risky anomalies. The first offering in the Semperis Lightning™ platform, IRP brings critical identity co...
ShapeBlue, a pioneer in delivering CloudStack engineering services and support, announces a partnership with proIO, a German Private Cloud Provider empowering SMBs across various industries through its Infrastructure-as-a-Service and Managed Hosting solutions. This collaboration marks a milestone in advancing cloud infrastructure and support for organisations in the region, implementing Apache CloudStack as their IaaS platform. Fully managed IaaS solution Both companies recognise the benefits...
DigiCert, a major global provider of digital trust, reconfirmed its commitment to standards and compliance with the successful completion of 31 audits within a 12-month period. These audits include a range of crucial certifications, including the SOC 2 Type II audit for DigiCert® DNS Trust Manager and the ETSI audit for DigiCert CertCentral® Europe, underscoring DigiCert's dedication to ensuring robust security measures and regulatory adherence across its offerings, around the world. S...