Cyber security - News
Whether it’s the optimal use of drones, the latest developments in cybersecurity, or innovative ideas for protecting financial institutions: Security Essen's supporting programme offers valuable knowledge, concrete strategies, and actionable recommendations for current challenges. The leading security trade fair, featuring around 500 exhibitors, will take place at Messe Essen from September 17 to 20. Throughout the event, industry professionals can network with top security experts in lec...
In the spirit of shared learning and growth, Gallagher Security is calling all security professionals and users to add their voices to an industry-wide survey designed to capture a snapshot of this transformative period. This collaborative research initiative seeks to gather global insights that will culminate in a comprehensive trends report designed to benefit every corner of the global security industry. Security Industry Trends Report “This project is rooted in one of our core...
Less than half of businesses using 1st generation Multi-Factor Authentication (MFA) do so because they believe it to be the most secure option available, new research from IDEE has revealed. The cybersecurity firm commissioned an independent survey of more than 500 IT and cybersecurity professionals within UK businesses. It found that 95% of UK businesses use 1st gen MFA solutions in some form, but just 40% of those said they used it because it was deemed to be the most secure cyber s...
Halftime in the run-up to the next INTERSCHUTZ (1 to 6 June 2026 in Hannover): the next edition of the world’s pioneering trade fair for the fire and rescue services, civil protection, safety, and security opens its doors in two years. The focus topics have already been finalised. Alongside the impacts of climate change and a turning point in civil protection, the spotlight will also be on the integration of artificial intelligence (AI) in control centers, situation centers, and at the sc...
Verkada, a pioneer in cloud-based physical security solutions shared the results of its 2024 State of Cloud Physical Security report. Based on insights from IT and physical security pioneers across various sectors, the findings look at current trends, insights, and challenges within the industry as it transitions from on-premises setups to cloud-based ones. Key findings Key findings of the Verkada’s 2024 State of Cloud Physical Security report include: A...
RiverSafe, an Application Security, DevOps, and Cyber Security professional services provider, has partnered with Checkmarx, the industry pioneer in cloud-native application security for the enterprise, to help organisations fortify their security landscape amid rising global threats. Open-source vulnerabilities A recent report unveiled concerning statistics. 84 percent of codebases contain open-source vulnerabilities, with 91 percent featuring outdated components, demanding heightened securit...
The Entrust Cybersecurity Institute released survey findings on the state of Zero Trust adoption and encryption in 2024. Entrust’s eighteenth annual study conducted by the Ponemon Institute reveals that the risk of a cyber breach is the number one global driver for Zero Trust strategy implementation. Zero Trust security practice “With the rise of costly breaches and AI-generated deepfakes, synthetic identity fraud, ransomware gangs, and cyber warfare, the threat landscape is...
Logpoint is announcing that Mikkel Drucker has been appointed new Chief Executive Officer at Logpoint. The nomination of Drucker marks the next stage in Logpoint’s journey to becoming a European cybersecurity powerhouse, providing regional access to outcome-driven security operations and compliance technologies. Drucker is an international technology executive with a strong focus on commercial excellence and a proven track record of successfully scaling SaaS and scale-up companies an...
Over one-third (35 percent) of Chief Information Security Officers (CISOs) admit to ignoring the National Cyber Security Centre’s (NCSC’s) cybersecurity guidance. This finding and others were revealed in a new survey and report from Absolute Security, a global pioneer in enterprise cyber resilience. Cyber Resilience Report 2024 This finding was despite 48 percent of respondents revealing that their organisation was hit by a ransomware attack over the past year. The NCSC has issued...
As the cybersecurity landscape evolves with the looming threat of quantum computing, industry pioneers are joining forces to develop robust solutions. The Hyperform consortium unites several pioneering players in cybersecurity and post-quantum: IDEMIA Secure Transactions, a project coordinator and a pioneering provider of secure solutions, CryptoNext, a provider of post-quantum cryptography remediation solutions, Atempo, a provider of data protection solutions, Prim’X, a software publ...
Crossword Cybersecurity Plc, the cybersecurity solutions company focused on cyber strategy has signed a partnership agreement with Boost, the key operations and logistics partner across Croatia, servicing multiple international markets. Through this partnership, Boost will distribute Crossword’s full suite of cybersecurity products across Europe. Boost will support Crossword, by providing clients with its ISO audit accreditation support services, enabling them to receive I...
Sentrycs – a global technology major in the cyber-based RF segment of counter-drone solutions – announced strategic deals that will see the implementation of its advanced counter-UAS (Unmanned Aerial Systems) solutions across multiple military bases throughout Europe. The field-proven Israeli technology provider will enable its customers to mitigate the immediate threats from small and commercial drones performing ISR (Intelligence, Surveillance, and Reconnaissance) missions over se...
BSRIA, the research and information membership body for the built environment, has appointed a new Chief Executive Officer, Lisa Ashworth, who is tasked with furthering BSRIA's impressive growth ambitions. Lisa Ashworth Ashworth joins BSRIA with a wealth of experience in pioneering technology-based data and information businesses. With an illustrious career marked by her tenure at organisations such as the Financial Times, PR Newswire, Frost and Sullivan, and Reevoo/Feefo, Ashworth brings a su...
Speakers at the 10th ETSI/IQC Quantum Safe Cryptography Conference have called on organisations to prepare their cybersecurity infrastructures to address the challenges of a post-quantum world. Organised by ETSI and the Institute for Quantum Computing, this year’s conference was hosted from 14-16 May by the Centre for Quantum Technologies (CQT), National University of Singapore (NUS), in partnership with the Infocomm Media Development Authority (IMDA) and the Cyber Security Agen...
Microsoft Azure customers in the United Arab Emirates now gain access to the StreamSets data integration platform with the scalability, reliability, and agility of Azure. StreamSets, a Software AG company, announced the availability of the StreamSets platform in the Microsoft Azure Marketplace, an online store providing applications and services for use on Azure, in the United Arab Emirates (UAE). Data integration capabilities StreamSets customers in the UAE can now take advantage of stronger...
The Cyber Leader Summit, held at London’s Leadenhall Building and hosted by Check Point® Software Technologies Ltd., a pioneering AI-powered, cloud-delivered cyber security platform provider, served as a forum for discussing the escalating threats in the cyber landscape, with a particular focus on the alarming rise in cybercrime and the critical need for more robust defences. The one-day event brought together over 200 delegates, along with experts from Check Point, Microsoft, Om...
Logpoint has been named a Niche Player in the 2024 Magic Quadrant for Security Information and Event Management (SIEM) by Gartner, the independent industry analyst firm. Logpoint has been recognised in every Magic Quadrant for SIEM since 2018. Logpoint offers a Converged SIEM solution that comes with native Security Orchestration, Automation & Response (SOAR). The solution offers Threat Detection, Investigation & Response (TDIR) and compliance use cases, helping organisations increase...
Matrix successfully demonstrated its cutting-edge security products and solutions at InnoMetro 2024, held from May 21st to 22nd at the Hotel Taj Vivanta. As a pioneering Indian company, Matrix proudly presented its RDSO 6.0-compliant network cameras, specifically designed for Indian Railways, at Booth No. H1.17. During the event, Matrix highlighted its commitment to cybersecurity with network cameras certified by STQC, Delhi lab, adhering to OWASP ASVS 4.0 L2 norms. These cameras ensure the s...
Market Logic Software, the pioneer in insights management solutions announced the launch of DeepSights™ API. DeepSights is the first AI assistant trained to provide accurate, relevant answers to business questions about markets and consumers. By using the new API to integrate DeepSights seamlessly with any business application, enterprises can infuse invaluable insights into their business processes and as a result, systematically drive better decision-making. Higher quality respons...
Northern Data Group's GenAI cloud platform, Taiga Cloud, a pioneering European generative AI cloud service provider (CSP) and VAST Data, the AI data platform company, announced a strategic partnership. Together, Taiga Cloud and VAST will deliver dedicated, scalable generative AI cloud services to Europe, driven by 100 percent carbon-free energy. Gartner predicts that by 2030, AI could consume up to 3.5 percent of the world's electricity. To meet this growing demand, organisations are seeking&nb...
UK Prime Minister Rishi Sunak has announced that 16 major international companies have committed to new voluntary international AI standards established at the Bletchley Park summit. These standards aim to foster transparency, accountability, and research the risk in AI development. Developing AI safety standards Roman Kucera, Chief Technology Officer at Ataccama, commented, “Six months is relatively little time to show significant progress, but the international commitment to maintaini...
Infosecurity Europe, the most influential information security event running at ExCeL London from 4-6 June 2024 announced further findings from its 2024 Cybersecurity Trends, Obstacles, and Opportunities report highlighting that ransomware and AI-generated attacks are weighing heavily on cybersecurity pioneers’ minds, with almost 40% of those surveyed stating these issues were accelerating investment into cyber defences. This emphasises the urgency for organisations t...
Smart Axiata, the mobile network operator in Cambodia, has announced the successful launch of the Next Generation Signalling Firewall (NGSF) and Intrusion Detection System (IDS) in collaboration with SecurityGen, a global telecom cybersecurity firm. These cutting-edge systems mark a significant milestone in Smart’s ongoing efforts to safeguard its network infrastructure and protect customer data. NGSF The NGSF is not just a defence mechanism; it serves as a bastion of network security,...
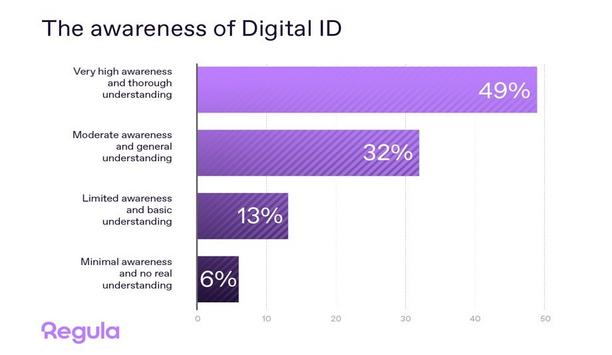
As more countries adopt the concept of digital identity, regulators are keen to showcase their plans and successes. But what do businesses think about this shift? To find out, Regula, a global developer of forensic devices and identity verification (IDV) solutions, commissioned a study to survey companies across different regions and industries to get a sense of their readiness, concerns, and expectations for digital identities. Digital identity Digital identity is considered to be a way to i...
When it comes to cybersecurity, the economy is relying too heavily on defensive measures and neglecting self-assessments using autonomous penetration testing solutions to assess its cyber resilience. This is the criticism of Rainer M. Richter, Head of Europe and Asia at the cybersecurity company Horizon3.ai. He points out that the European Central Bank (ECB) has been conducting stress tests to measure cyber resilience in the financial sector for years. "Companies in all sectors would be well ad...
An air of excitement circled the Gallagher Security booth at the recent TSE event in Birmingham, as the award-winning, global security manufacturer demonstrated the latest innovations in their security ecosystem. The annual event, held from 30 April – 2 May which attracted more than 14,000 visitors to Birmingham’s NEC, brought together manufacturers, distributors, installers, consultants, and end users, and displayed the latest products, tech...
TraiCon Events will be hosting Botswana’s premier cybersecurity event titled “Cyber Revolution Summit” scheduled on 9th August 2024 in Gaborone, Botswana. This summit will feature keynote presentations and panel discussions with top security experts from various industries covering a range of topics, including cybersecurity innovations, data privacy & security, risk management, network security, threat detection & intelligence, and vulnerability management. ...
Hospitals are turning to video technology to enhance patient care and safety with the rising demand for healthcare services and the ongoing battle against staffing shortages. However, hospitals looking to expand their video technology must ensure their surveillance systems are compliant with the Health Insurance Portability and Accountability Act (HIPPA). Being HIPAA compliant helps protect patient privacy and safeguard sensitive health information. This is non-negotiable in the digital age. Wi...
Global law firm Clifford Chance announced that it is participating in a Department of Commerce initiative to support the development and deployment of trustworthy and safe Artificial Intelligence (AI). Established by the Department of Commerce’s National Institute of Standards and Technology (NIST) on February 8, 2024, the U.S. AI Safety Institute Consortium (AISIC) brings together AI creators and users, academics, government and industry researchers, and civil society organisat...
Oakdoor, a pioneer in hardware-enforced security solutions, which is part of PA Consulting (PA), and Nexor, the pioneering specialist in Secure Information Exchange, have announced a strategic partnership to advance a high assurance cross-domain solution for secure data sharing. The partnership will start to create highly integrated software guarding and hardware verification solutions – with the aim of making access to data more secure and manageable for customers using multiple security...