Kingston Technology Company, Inc. - Experts & Thought Leaders
Latest Kingston Technology Company, Inc. news & announcements
Kingston Digital, Inc., the Flash memory affiliate of Kingston Technology Company, Inc., a global provider of memory products and technology solutions, announced it will showcase an array of products at Global Security Exchange (GSX) (booth 2685 Central Hall), the most established trade event for security professionals. The company will display its full line of industry-leading encrypted USB Flash drive solutions, including the IronKey brand purchased in 2016, as well as upcoming high-density business and enterprise SSDs and Server Premier memory. “When it comes to memory and data storage solutions, it is imperative that security professionals trust the products they use and the companies that make them. For over 30 years, we have been an unquestioned leader in this field,” said Richard Kanadjian, encrypted USB business manager, Kingston. “For storage-bound applications, Kingston stands ready as the industry shifts away from traditional 15k SAS toward NVMe, where the performance gains in terms of IOPS and lower latency is tremendous. GSX is the perfect venue for us to show the security industry our ability to provide it with the most complete line of superior data performance solutions for their varied security, data, audio/video or other applications.” GDPR compliant USB drives Kingston encrypted USB drives are designed to protect data that require high security and serve as an additional element in compliance with the EU’s GDPR GSX 2018 takes place at the Las Vegas Convention Center from September 23-27. Kingston is located in booth #2685 in the Central Hall. Kingston encrypted USB drives are designed to protect data that require high security, maintain a productive and efficient mobile workforce, and serve as an additional element in compliance with the EU’s GDPR (General Data Protection Regulation). These drives help users meet specific agency directives, such as encryption, TAA and FIPS compliance, and are ideal for government or corporate use. The line includes both IronKey drives available in 4GB to 128GB capacities; and, Kingston DataTraveler models available from 4GB to 64GB. Securing data with SSDs In business applications, Kingston SSDs increase performance, help secure data, and extend the life of older systems. In enterprise applications, Kingston SSDs offer increased reliability and power fail features to keep mission-critical environments up and running 24/7. The upcoming DC500R is a high-performance 6 Gbps SATA SSD designed for read-centric data-centre workloads. It is designed with strict QoS requirements to ensure predictable random IO performance as well as predictable latencies over a wide range of read/write workloads. Special power-loss safeguards help reduce the likelihood of data loss and ensure that the drive will successfully re-initialise on the next power-up of the system. DC1000M U.2 NVMe SSD The DC1000M 2.5″ U.2 NVMe SSD's advanced architecture enables delivery of up to 600k IOPS of random read performance and a potent 3GB/s of throughput The DC1000M 2.5″ U.2 NVMe SSD features high-storage capacity and best-in-class enterprise performance. Its high-performance Gen 3.0 x4 PCIe NVMe interface enables high throughput and low latency on a standardised low-cost platform. The drive’s advanced architecture enables delivery of up to 600k IOPS of random read performance and a potent 3GB/s of throughput. Its strict QoS requirements ensure predictable random IO performance as well as predictable latencies over a wide range of workloads. The ‘mixed-use’ workload drive makes it ideal for running a wide range of applications. Kingston server memory is a worldwide industry standard. Server Premier modules are manufactured using a locked bill of materials (BOM). They are designed for big data centres, people who implement high-quality branded provisioned servers to those who use or build white-box systems and require a consistent brand and revision of DRAM. The line offers a variety of embedded memory products that provide maximum performance and flexibility
Kingston Digital, Inc., the Flash memory affiliate of Kingston Technology Company, Inc., the independent world leader in memory products, is set to appear at the upcoming 63rd ASIS International Annual Seminar and Exhibits (ASIS 2017), the premier event for security professionals. Kingston products on display will include its full line of Encrypted USB Flash drives, SSDs and its Server Premier memory. Additionally, the company will have demonstrations highlighting the rugged capabilities of its IronKey products and the extreme performance capabilities of its upcoming DCU1000, the industry’s fastest PCIe NVMe SSD for the U.2 form factor. “We look forward to being part of ASIS 2017, as it gives us a tremendous opportunity to show security professionals from around the world the many products that make up the Kingston family, and how each one provides users with rock-solid reliability, ultimate security and maximum power,” said Ken Campbell, encrypted USB business manager Kingston. “When visitors leave our booth, we want them to fully understand Kingston’s commitment to offering the most complete family of data performance solutions.” Kingston Encrypted USB Drives Kingston encrypted USB drives are designed to protect data that requires high security. These drives help users meet specific agency directives, such as TAA and FIPS compliance, and are ideal for government or corporate use. The line includes both IronKey and DataTraveler models. Kingston Solid State Drives (SSD) Kingston makes SSDs for business, enterprise, and system-builder applications. In business applications, Kingston SSDs increase performance, make data more secure and can be used to extend the life of older systems. In enterprise applications, Kingston SSDs offer increased reliability and power-failure features to keep mission-critical environments up and running 247. In system-builder applications, Kingston SSDs serve as hard-drive replacements ideal for non-PC applications. Kingston Server Memory Kingston server memory is a worldwide industry standard. Our Server Premier modules are designed for big data centers, people who implement high-quality branded provisioned servers to those who use or build white box systems and require a consistent brand and revision of DRAM.
Insights & Opinions from thought leaders at Kingston Technology Company, Inc.
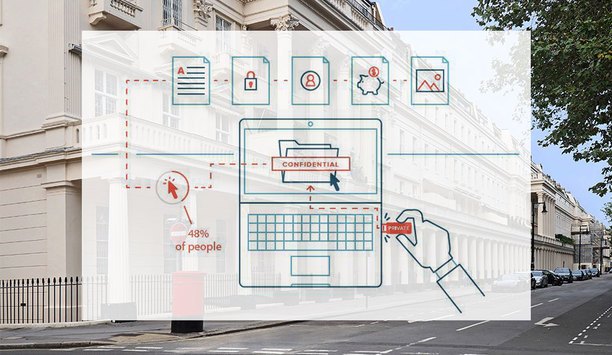
Cybersecurity involves a variety of risks and vulnerabilities to the enterprise, from distributed denial of service (DDoS) attacks to phishing to USB drives. Companies may also be at risk from use of interactive kiosks, or even from cyberattacks against traveling executives. Preventing phishing and cyberattacks The 'Management Hack' service is designed for C-level executives, such as CEO, CFO or event CIO Phishing is a fraudulent attempt to gain sensitive information such as user names, passwords or credit card details by disguising as a trustworthy entity in an electronic communication. These are among the most dominant forms of social engineering attacks. To avoid phishing attacks, NTT Security has expanded their suite of phishing attack simulation services using special social engineering techniques to check whether senior executives pose a security risk. The 'Management Hack' service is designed for C-level executives, such as CEO, CFO or event CIO. These executives are more likely to have unrestricted access to highly confidential company data, which makes them a valuable target. Simulated, personalised social engineering attacks are carried out, with the individuals involved unaware they are being targeted. NTT then analyses how executives respond, identities weaknesses, and recommends appropriate measures such as awareness training. Cybersecurity helps deter phishing and DDoS attacks ADT Cybersecurity partners with Cofense phishing defense solutions to offer phishing detection and response. Cofense Triage is a phishing-specific automated incident response platform that works as part of ADT Cybersecurity managed services. The system focuses on thwarting phishing attacks before they can cause damage by moving detection of such attacks up the kill chain. Data breaches caused by cyberattacks on networks are plaguing businesses of all sizes. The median time of compromise to discovery is 80 days, with the average cost of data breach costing organizations $3.62 million. Managing endpoint security There is a need for cybersecurity to extend beyond the firewall Another cybersecurity vulnerability for companies is the unauthorised use of USB ports. There is a need for cybersecurity to extend beyond the firewall, which requires restricting access to a system’s USB ports as a means of managing 'endpoint security.' However, blocking all USB ports can restrict productivity, and employees are not as efficient as they should be. A solution is the use of more encrypted USB drives to combine the productivity advantages of allowing USB access while protecting the information on the drives. Kingston Technology offers hardware-based encrypted USB drives that uses AES 256-bit encryption in XTS mode to ensure that if anyone finds a USB drive, they cannot access the information. Illustrating the value of encrypted drives was an incident when a USB drive from Heathrow Airport was found on a London street. It contained confidential information about accessing restricted areas at the airport and security measures used to protect the Queen. Data security and interactive kiosks Another possible cybersecurity vulnerability is use of interactive kiosks, which are computer terminals that feature specialised hardware and software that provide access to information and applications. Kiosks are typically placed in high foot-traffic environments such as retail stores, hospitals, banks, hotels, airports, courthouses, libraries and railway stations. A kiosk is particularly attractive to attackers because they know the security might not be as tight as it should be. Making kiosks more secure could be the difference between you being breached and remaining safe. A kiosk is attractive to attackers because they know the security is not very tight Executives who travel are another vulnerability to be considered. The international cybersecurity landscape has grown increasingly dynamic, with threats posed by government authorities (in some countries), terrorists, insurgents, and criminals, requiring travelers to be proactive and vigilant. U.S. citizens, particularly executives of U.S.-based technology companies, must be aware that they are considered high-value targets for nation-state intelligence services and criminally-motivated bad actors.Traveling executives should avoid using public Wi-Fi services—unless they use private VPN service for encryption WiFi and wireless connectivity There has been a shift from 'thrill hacking,' to an increase of 'hacking as a business' (through credential compromise and ransomware), to an increase in 'hacking for harm' - with the rise of 'nuke ware' and ransomware without a clear financial motivation. Traveling executives should avoid using public Wi-Fi services—unless they use private VPN service for encryption. They should also increase the privacy setting on technical devices and disable location identifiers. Other precautions include creating a new (unlinked) email for internet correspondence and use of temporary (i.e., burner) phones to protect data and contacts. Travelers should also consider purchasing international MyFi devices to decrease the risk of getting Personal Identification Information (PII) or Protected Healthcare Information (PHI) stolen.
A USB drive from Heathrow Airport, found on a London street in late October, contained confidential information about accessing restricted areas at the airport and security measures used to protect the Queen. The drive also contained a timetable for anti-terrorism patrols at the airport and documentation of the ultrasound system used by Heathrow security to check perimeter fences and runways for breaches. The data was not encrypted, and the London resident who found it turned it over to a newspaper reporter. How cybersecurity impacts physical security The incident highlights a number of issues for security professionals. One is the interrelated nature of cybersecurity and physical security, and how a failure of one can directly impact the other. Another is extending cybersecurity outside the firewall, considering the inherent risks of USB drives and the need to manage “endpoint security,” such as restricting access to a system’s USB ports. An important security failure in the case of the Heathrow incident was lack of encryption of the USB drive, says Ruben Lugo, Strategic Product Marketing Manager at Kingston Technology, which provides a line of USB drives with hardware-based encryption. “If you block out all the USB ports, it can restrict productivity, and employees are not as efficient as they should be,” says Lugo. He says companies should be using more encrypted USB drives to combine the productivity advantages of allowing USB access while protecting the information on the drives. Data protection regulations Protection of data – whether inside the firewall or outside – is increasingly important in an age of greater cybersecurity regulation. The European Union's General Data Protection Regulation (GDPR) creates new safeguards and requirements for protecting personal data, with a compliance deadline of May 25, 2018, after which noncompliance can result in expensive fines. A disgruntled employee used a USB drive to steal banking information for 30,000 people, as published by Tom Brant in: “Report: FDIC Employees Caused Repeated Security Breaches,” PC Magazine, July 15, 2016 Regulations also include New York State's 23NYCR500 cybersecurity requirements that financial services companies protect customer information and related IT systems. The New York regulation requires each company to assess its specific risk profile and design a programme to address its risks, ensuring the safety and soundness of the institution and protecting customers. Hardware-based encryption Providing a cybersecurity tool, Kingston highlighted its hardware-based encrypted USB drives at the recent ASIS show in Dallas. A USB drive with hardware-based encryption is self-contained and doesn’t require a software element on the host computer. No software vulnerability eliminates the possibility of brute-force, sniffing and memory hash attacks. Digitally signed firmware cannot be altered, and there is a physical layer of protection, too. The drives come in epoxy-dipped/filled cases that prevent access to the physical memory. In contrast, a USB drive with software encryption uses software that runs on the host computer and is vulnerable to attacks. The use of AES 256-bit encryption in XTS mode ensures that anyone who finds a USB drive, such as the man in London, cannot access the information. The drive wipes itself clean after 10 attempts of guessing the password. “Encrypted drives are not complicated,” says Lugo. “They are a simple solution that anyone can implement.” Kingston’s encrypted USB drives are priced between $40 and $600, depending on the capacity and covering needs ranging from a small business owner to military- and government-grade products. Kingston also provides products for use inside the firewall, including business and enterprise solid state drives (SSDs), offering high density and extreme performance, and their server premier DRAM memory products providing performance and flexibility. To learn more about Kingston, please visit www.kingston.com
One system, one card
DownloadAligning physical and cyber defence for total protection
DownloadUnderstanding AI-powered video analytics
DownloadEnhancing physical access control using a self-service model
DownloadHow to implement a physical security strategy with privacy in mind
Download