 |
| Done right, a good metric programme will help tell the story of the security department |
Knights of medieval times are known for impossible quests and challenging missions seeking rare religious items. The quest for the Holy Grail is perhaps the most notable. Today’s security professionals are often on their own quest, seeking what sometimes feels like the impossible – the search for perfect security metrics!
What are metrics and are they really that hard to find? Metrics are simply a measure to show effectiveness or to track performance. We are surrounded by metrics every day. For someone who wants to lose weight, a daily stop on the scale to track progress is an example of a metric. For someone interested in building muscle, the metric used may be the amount lifted in a bench press or leg press. Companies use metrics to measure key progress in areas such as sales, repeat customers or net income.
Security metrics best defined by finance team
How do you measure the success of a security programme? If your security programme were primarily about preventing crime, you would need to track every time you deter a criminal – something that is very hard to know or track. Basically, it means tracking something that didn’t happen. There is good news though. There are other ways to measure success and to provide ways to showcase what the security programme has accomplished.
If there is one group that uses and understands metrics, it is the finance team of a business. The finance team deals with every part of an organisation and understands the value of setting targets and measuring progress, in terms of budget, income and expenses. We are going to look at security metrics used in one case study that came about after the security department reported to the CFO.
Understanding security metrics from the CFO
The CFO had several support groups reporting to him and was interested in how to track progress of each of the groups. It was quickly determined that there were four core areas to track. Activity, Efficiency, Quality and Customer Satisfaction were the categories focused on.
| Service Area | Background |
| Activity | Crime trends that pose a concern or need to be tracked; |
| Efficiency | Budget, of course. What else affects efficiency? |
| Quality | What makes the security department stand out? What |
| Customer Satisfaction | What makes employees feel safe at work? |
Security activity measurement
The first category was to measure overall activity. The specifics may change from one organisation to another, but looks at the types of responses and incidents handled by the security team. This should include general crime rates on campus, or may be a focus on specific issues. For example, in healthcare, a top priority has become the issue of violence and assaults on clinical staff by patients.
By nature, many of these metrics are lagging metrics. In other words, the metric is a measurement of something that already happened. However, it is possible to include leading metrics as well. Leading metrics are a measurement of an activity that is pro-active or preventative in nature. An example of a leading metric could be tracking the number of exterior patrols done by security officers. The theory being highly visible and pro-active patrols are a deterrent and reduce overall crime on campus. For a system integrator, regular maintenance of access control or video systems that prevent downtime could be a measure of a leading indicator instead.
Financially efficient security programme
Efficiency was the next category. Of course, since this was coming from the CFO, financial efficiency was involved. One metric was budget compliance, a ratio of budgeted funds versus actual spend as a percentage. Another efficiency number tracked was the number of voluntary turnovers. This number tracked how many security employees left for other pursuits. It did not include involuntary turnover, as it was felt that this could potentially influence leaders to keep unsavoury employees to limit the turnover data. Other examples of efficiency could include storage of valuables for guests or patients, or number of lost items returned to the owner.
Quality of security programme
The next category considered was quality. To track the quality of the security program, a variety of options were considered. In this case, the number of security employees who received certification in the industry was tracked. The CFO also wanted to see the security department provide, or at least facilitate, security training for staff. The metric used was the number of training sessions provided to staff, including brief internal education meetings with different departments or ‘brown bag’ lunch and learn sessions that could include outside speakers. Again, education sessions were a more pro-active measure and could be considered a leading indicator.
Customer satisfaction
A metric is something that you are going to want to measure on a regular basis and if the work involved getting that number is too difficult, it will quickly be ignored or left undone and you end up having no measure at all |
The last area considered in this example was customer satisfaction. Fortunately, there were several options from which to choose. One vital measure was an annual survey that asked about staff perception of safety and security at the organisation. The scale was 1-5 and allowed to track the number in the top category, those who felt very safe at work. This was the measure used with the goal to move people from the next category, feeling somewhat safe, to the top or feeling very safe. Response time by the security team was another area that linked directly to customer satisfaction. There was also a secret shopper programme in place where an individual would contact security about a routine matter and provide feedback, scoring the officer on customer service and friendliness to the appearance of the officer’s uniform.
Importance of security metrics
Of course, tracking all of the metrics mentioned is great, but what does it really mean? Once you begin tracking results, the past results can be used as a baseline that allows you to set goals, establish targets moving forward, and identify areas of improvement. Keep in mind that these baselines are different from industry benchmarks. Benchmarks are comparisons or numbers based on a mix of different organisations, often within the same industry, to gauge where one company is in relation to the industry.
When selecting metrics there are a few things to keep in mind. Probably the most important is to make sure that the data you need for the metric is easily available. A metric is something that you are going to want to measure on a regular basis and if the work involved getting that number is too difficult, it will quickly be ignored or left undone and you end up having no measure at all. A good rule of thumb is that the data or measure should be able to be collected within 15 minutes.
Also, pick metrics that are something that the security team can act upon or have a direct impact on. If the measure reflects something that the security team has no control over, then it tells very little about the success or effectiveness of the security program. For example, neighbourhood crime stats may be valuable to track for awareness sake, but do not reflect on the security team’s performance so should not be included as part of the performance metrics.
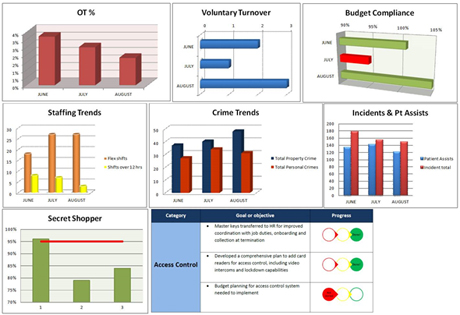 |
| (see bigger image) |
| Visuals and charts can be very helpful in seeing exactly what areas may need attention and what is going well |
Evaluating security metrics
The last word about metrics: be sure to do something with the metrics collected. Use the data to tell a story about what the security department is doing. Visuals and charts can be very helpful in seeing exactly what areas may need attention and what is going well. Keep evaluating the value of the metrics used as well. An idea that originally seemed great, may turn out to not really reflect what you had hoped and should be changed and a new metric identified instead. This is an ongoing process.
Done right, a good metric programme will help tell the story of the security department and highlight the successes as well as help identify potential areas for improvement.
Learn why leading casinos are upgrading to smarter, faster, and more compliant systems












